Replay Attack Detection Method Based on Auxiliary Information Compensation and Control Signal Coding
-
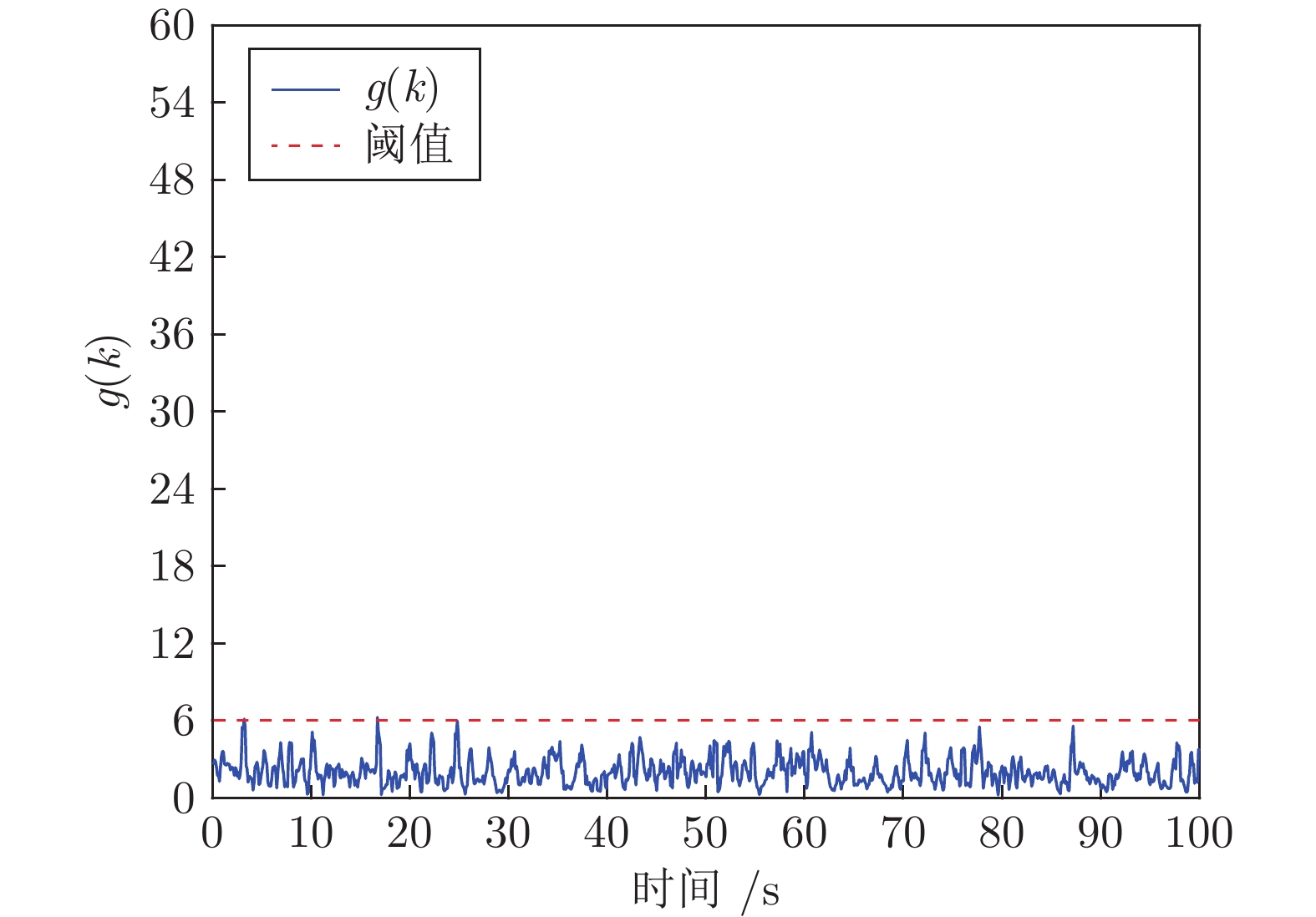
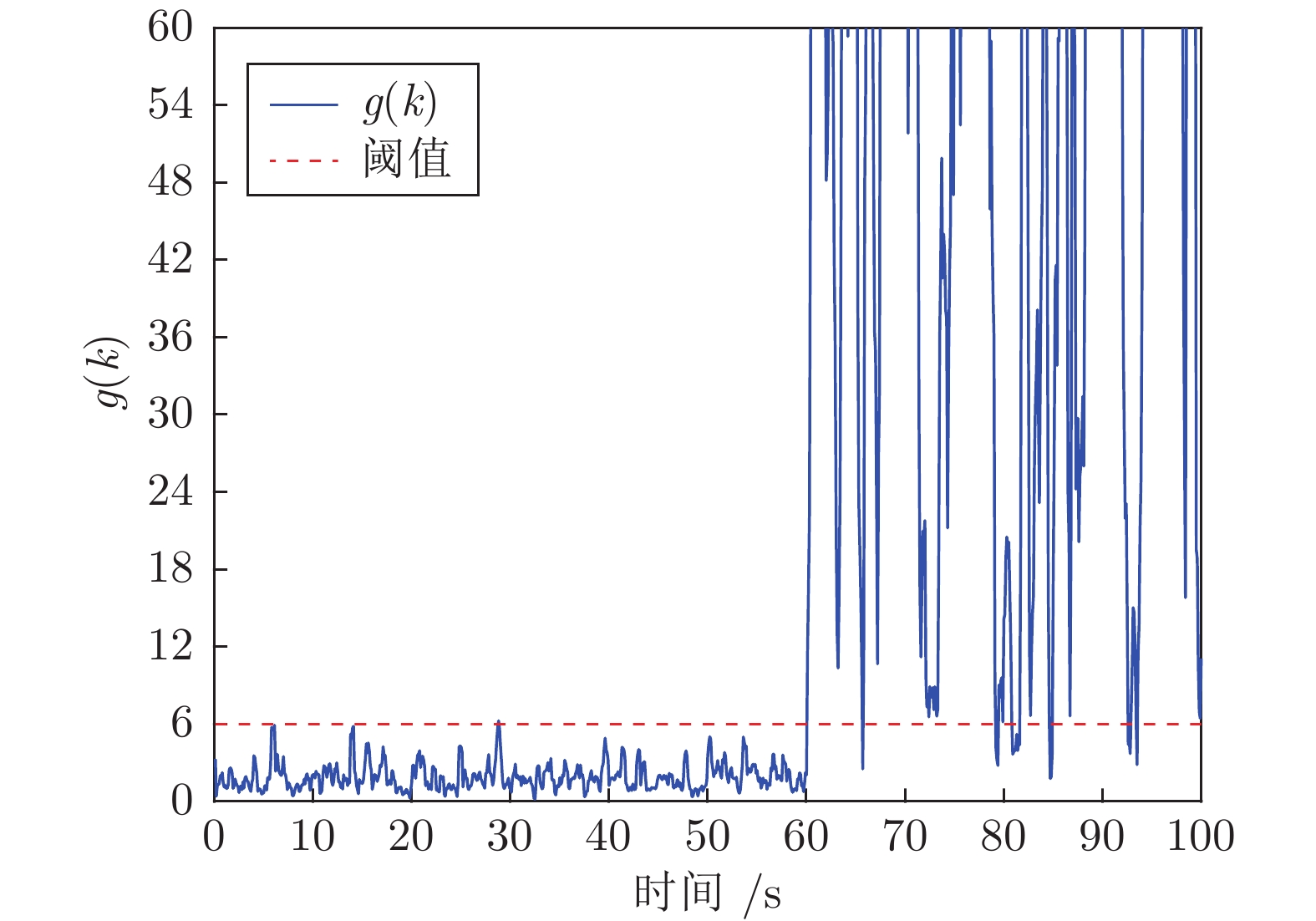
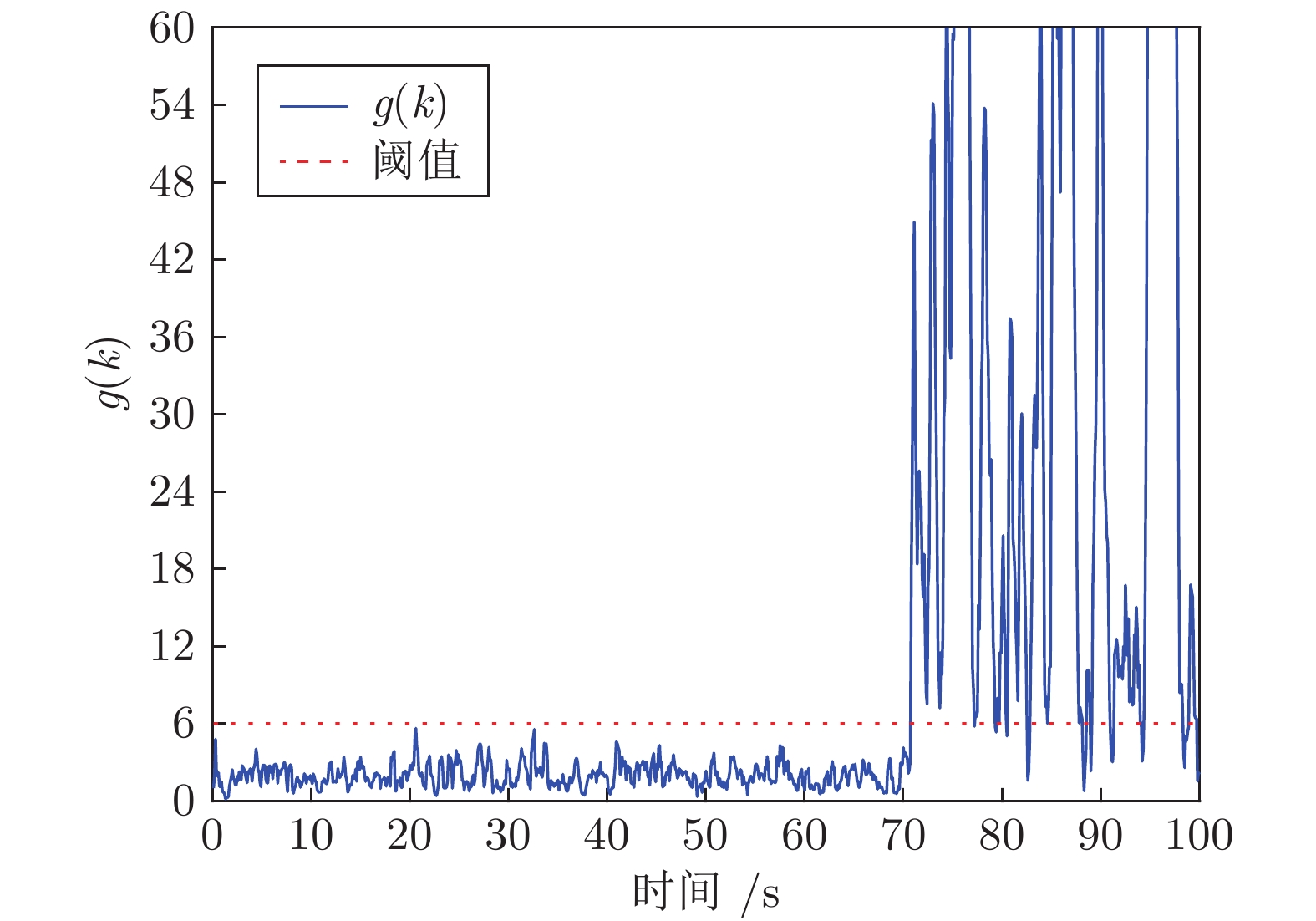
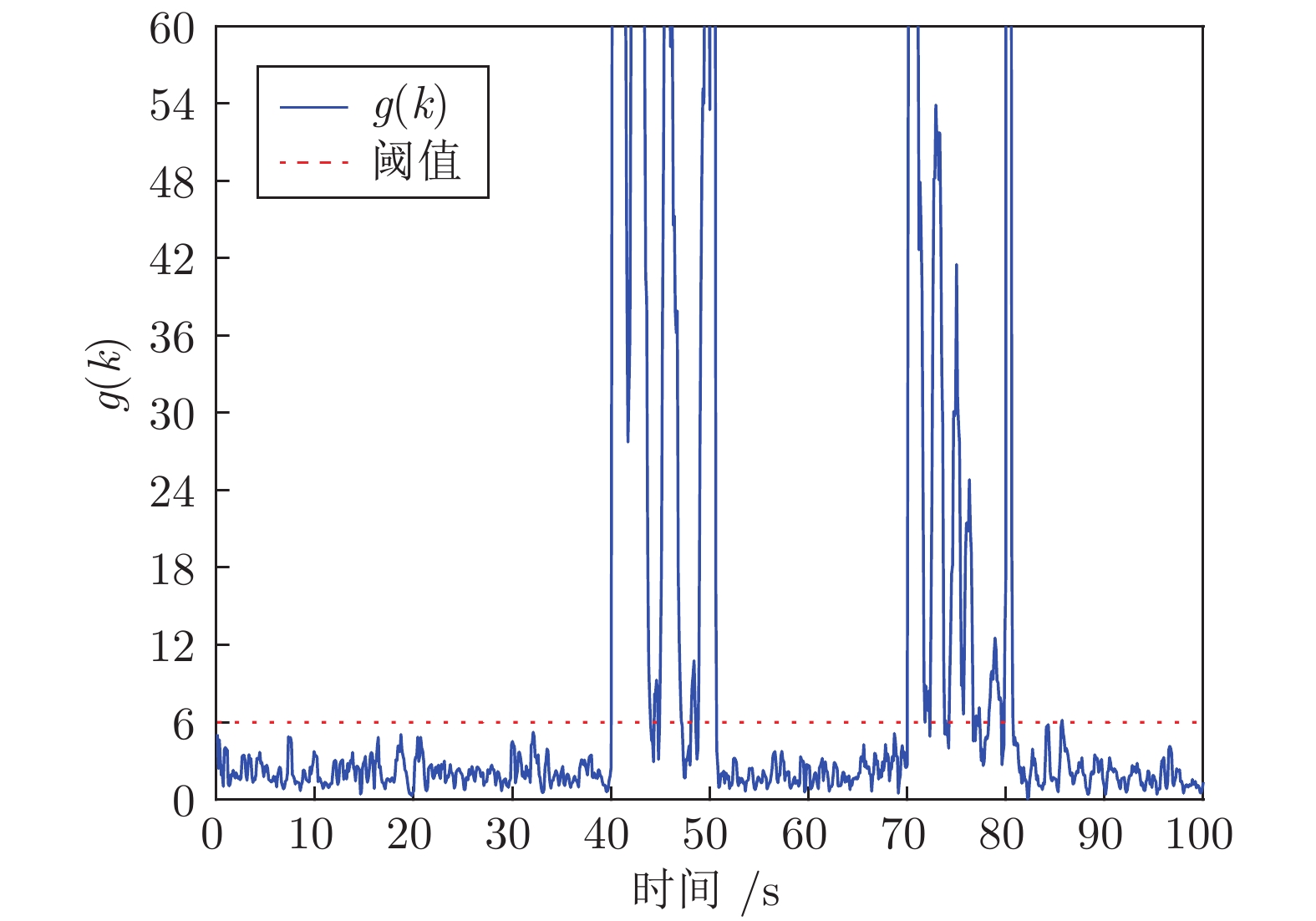
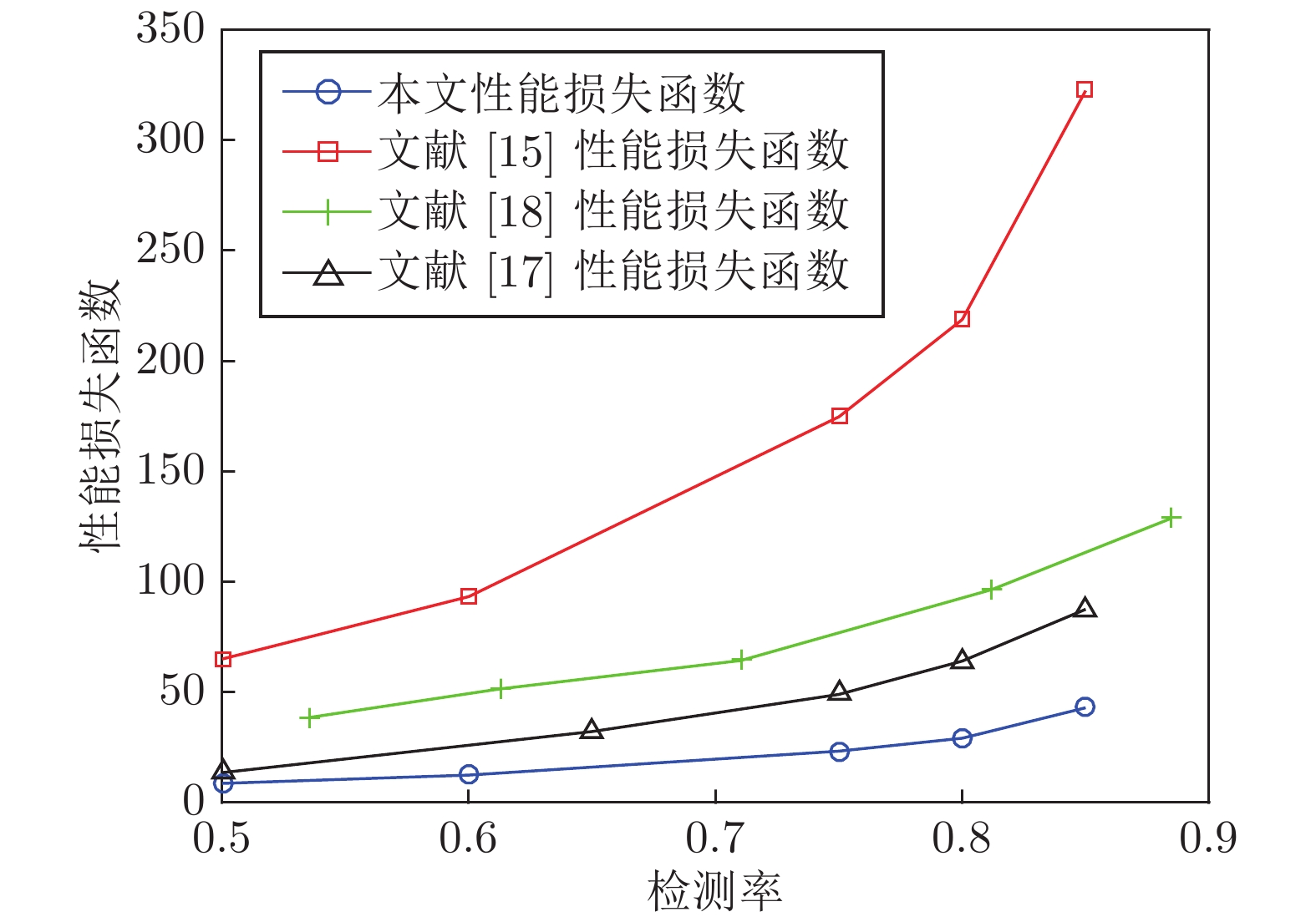
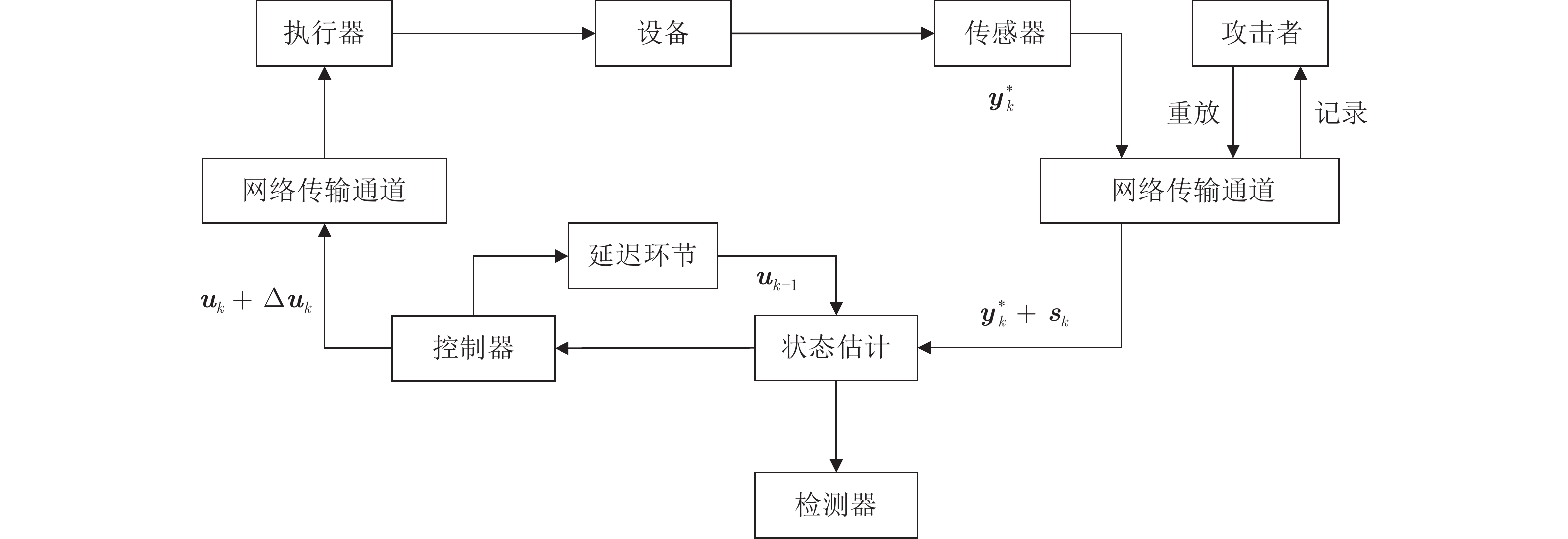
摘要: 向最优控制信号中加入编码信号是实现信息物理系统(Cyber physical system, CPS)重放攻击检测的有效方法, 但会造成系统控制性能的损失. 如何在保证重放攻击检测率条件下降低系统的控制性能损失是一个值得研究的问题. 为此, 提出一种基于辅助信息补偿的控制信号编码检测方法, 通过向测量值添加辅助信号补偿控制编码信号对最优状态估计的影响. 首先, 证明了此方案下重放攻击的可检测性, 导出检测率的上界与检测函数阈值间的定量关系. 其次, 证明了加入辅助信号后系统控制信号与未添加编码信息时相同, 之前时刻的控制编码信号不会造成累积效应. 因此, 系统当前时刻的控制性能损失仅与当前时刻编码信号的大小有关. 最后, 将编码信号的协方差矩阵、检测率和检测阈值之间的关系表示成一个最优化问题, 给出了编码信号方差的计算方法. 仿真结果表明, 本文方法能有效地检测重放攻击的发生, 且系统控制性能的损失较小.Abstract: Adding coding signal to the optimal control signal is an effective method to detect the replay attack in cyber physical systems (CPSs), which always causes loss of system control performance. How to reduce the sacrifice of system control performance and guarantee the detection rate of replay attack is a valuable problem to be studied. In this paper, a control signal coding detection scheme has been proposed based on auxiliary information compensation. By adding auxiliary signal to the system measurements, the influence of the coding signal on the optimal state estimation has been compensated. Firstly, the detectability of replay attack under the proposed scheme is proved, and the quantitative relationship between the upper bound of the detection rate and the threshold of the detection function is derived. Secondly, it is demonstrated that the control signal generated by the controller after adding auxiliary signal is the same as the control signal without coding signal. Therefore, the historical coding signal does not effect the system cumulatively. The loss of system control performance at current moment is only related to the size of the current coding signal. Finally, the relationship between the covariance matrix of the coding signal, the detection rate and the detection threshold is expressed as an optimization problem, through which the variance of the coding signal can be derived. Simulation results show that the attack can be effectively detected throught the proposed scheme, while the loss in the corresponding system control performance is relatively smaller.
-
Key words:
- Cyber physical system (CPS) /
- replay attack /
- attack detection /
- control signal coding
-
表 1 噪声方差及性能指标比较
Table 1 Comparison of noise variance and performance index of different schemes
-
[1] 刘烃, 田决, 王稼舟, 吴宏宇, 孙利民, 周亚东等. 信息物理融合系统综合安全威胁与防御研究. 自动化学报, 2019, 45(1): 5-24Liu Ting, Tian Jue, Wang Jia-Zhou, Wu Hong-Yu, Sun Li-Min, Zhou Ya-Dong, et al. Integrated security threats and defense of cyber-physical systems. Acta Automatica Sinica, 2019, 45(1): 5-24 [2] 李洪阳, 魏慕恒, 黄洁, 邱伯华, 赵晔, 骆文城等. 信息物理系统技术综述. 自动化学报, 2019, 45(1): 37-50Li Hong-Yang, Wei Mu-Heng, Huang Jie, Qiu Bo-Hua, Zhao Ye, Luo Wen-Cheng, et al. Survey on cyber-physical systems. Acta Automatica Sinica, 2019, 45(1): 37-50 [3] Kumar C, Marston S, Sen R. Cyber-physical systems security: state of the art and research opportunities for information systems academics. Communications of the Association for Information Systems, 2020, 47: 678-696 doi: 10.17705/1CAIS.04731 [4] Dibaji S M, Pirani M, Flamholz D B, Annaswamy A M, Johansson K H, Chakrabortty A. A systems and control perspective of CPS security. Annual Reviews in Control, 2019, 47: 394-411 doi: 10.1016/j.arcontrol.2019.04.011 [5] Humayed A, Lin J Q, Li F J, Luo B. Cyber-physical systems security—a survey. IEEE Internet of Things Journal, 2017, 4(6): 1802-1831 doi: 10.1109/JIOT.2017.2703172 [6] Ding D R, Han Q L, Xiang Y, Ge X H, Zhang X M. A survey on security control and attack detection for industrial cyber-physical systems. Neurocomputing, 2018, 275: 1674-1683 doi: 10.1016/j.neucom.2017.10.009 [7] Mousavinejad E, Yang F W, Han Q L, Vlacic L. A novel cyber attack detection method in networked control systems. IEEE Transactions on Cybernetics, 2018, 48(11): 3254-3264 doi: 10.1109/TCYB.2018.2843358 [8] Teixeira A, Shames I, Sandberg H, Johansson K H. A secure control framework for resource-limited adversaries. Automatica, 2015, 51: 135-148 doi: 10.1016/j.automatica.2014.10.067 [9] Zhang H, Cheng P, Shi L, Chen J M. Optimal DoS attack scheduling in wireless networked control system. IEEE Transactions on Control Systems Technology, 2016, 24(3): 843-852 doi: 10.1109/TCST.2015.2462741 [10] 彭大天, 董建敏, 蔡忠闽, 张长青, 彭勤科. 假数据注入攻击下信息物理融合系统的稳定性研究. 自动化学报, 2019, 45(1): 196-205Peng Da-Tian, Dong Jian-Min, Cai Zhong-Min, Zhang Chang-Qing, Peng Qin-Ke. On the stability of cyber-physical systems under false data injection attacks. Acta Automatica Sinica, 2019, 45(1): 196-205 [11] Sargolzaei A, Yazdani K, Abbaspour A, Crane C D, Dixon W E. Detection and mitigation of false data injection attacks in networked control systems. IEEE Transactions on Industrial Informatics, 2020, 16(6): 4281-4292 doi: 10.1109/TII.2019.2952067 [12] Franze G, Tedesco F, Lucia W. Resilient control for cyber-physical systems subject to replay attacks. IEEE Control Systems Letters, 2019, 3(4): 984-989 doi: 10.1109/LCSYS.2019.2920507 [13] Dan Y, Zhang T Y, Guo G. Stochastic coding detection scheme in cyber-physical systems against replay attack. Information Sciences, 2019, 481: 432-444 doi: 10.1016/j.ins.2018.12.091 [14] Mo Y L, Sinopoli B. Secure control against replay attacks. In: Proceedings of the 47th Allerton Conference on Communication, Control, and Computing. Monticello, MS, USA: IEEE, 2009. 911−918 [15] Mo Y L, Chabukswar R, Sinopoli B. Detecting integrity attacks on SCADA systems. IEEE Transactions on Control Systems Technology, 2014, 22(4): 1396-1407 doi: 10.1109/TCST.2013.2280899 [16] Tran T T, Shin O S, Lee J H. Detection of replay attacks in smart grid systems. In: Proceedings of the International Conference on Computing, Management, and Telecommunications. Ho Chi Minh City, Vietnam: IEEE, 2013. 298−302 [17] Liu H X, Mo Y L, Yan J Q, Xie L H, Johansson K H. An online approach to physical watermark design. IEEE Transactions on Automatic Control, 2020, 65(9): 3895-3902 doi: 10.1109/TAC.2020.2971994 [18] Zaman A, Safarinejadian B, Birk W. Security analysis and fault detection against stealthy replay attacks. International Journal of Control, 2020, DOI: 10.1080/00207179.2020.1862917 [19] Fang C R, Qi Y F, Cheng P, Zheng W X. Cost-effective watermark based detector for replay attacks on cyber-physical systems. In: Proceedings of the 11th Asian Control Conference. Gold Coast, Australia: IEEE, 2018. 940−945 [20] Fang C R, Qi Y F, Cheng P, Zheng W X. Optimal periodic watermarking schedule for replay attack detection in cyber-physical systems. Automatica, 2020, 112(5): Article No. 108698 [21] Guan F X, Jiang Q. Experiment of Control System Simulation. Beijing: Tsinghua University Press, 2015. 122−123 -




 下载:
下载: