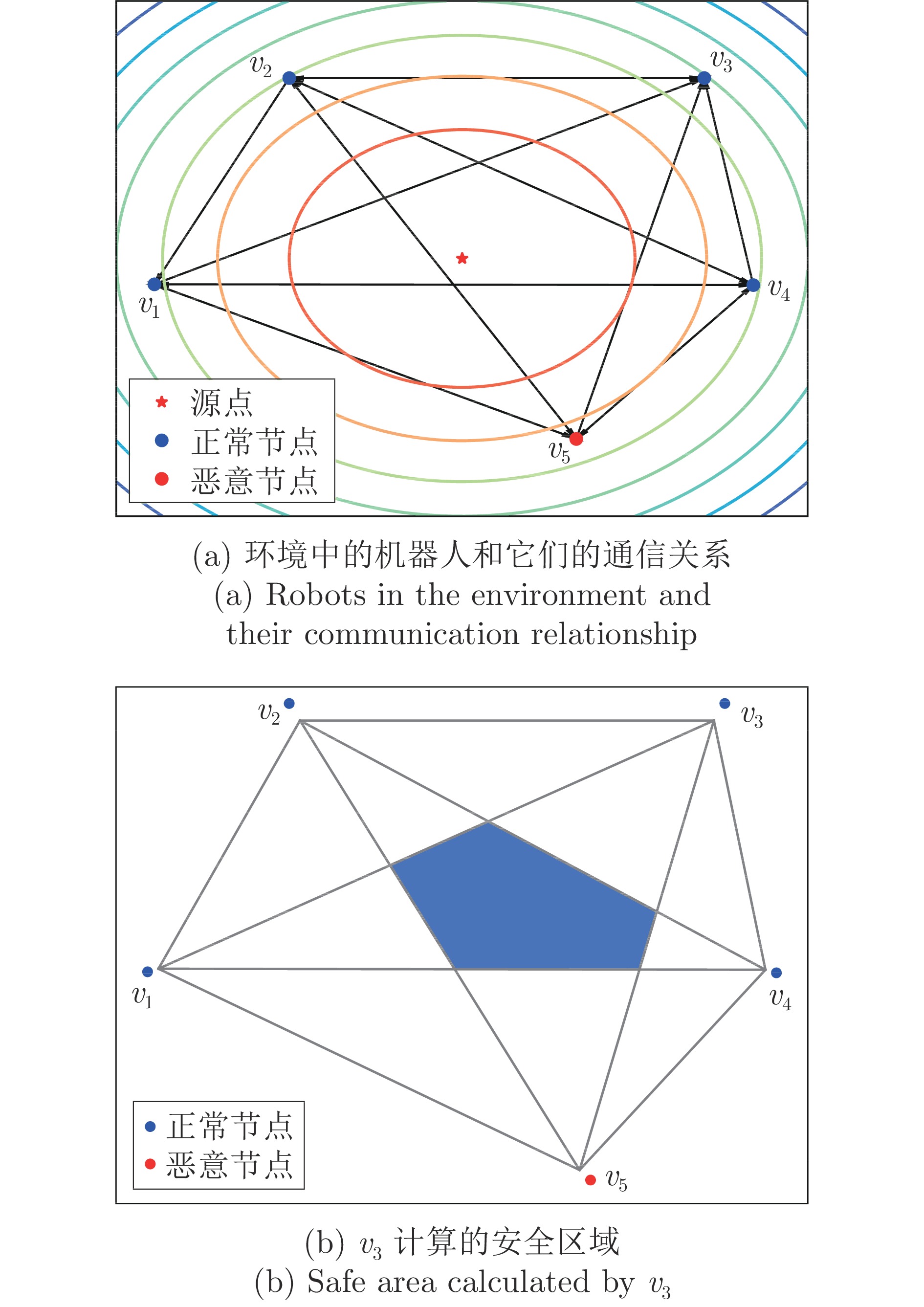
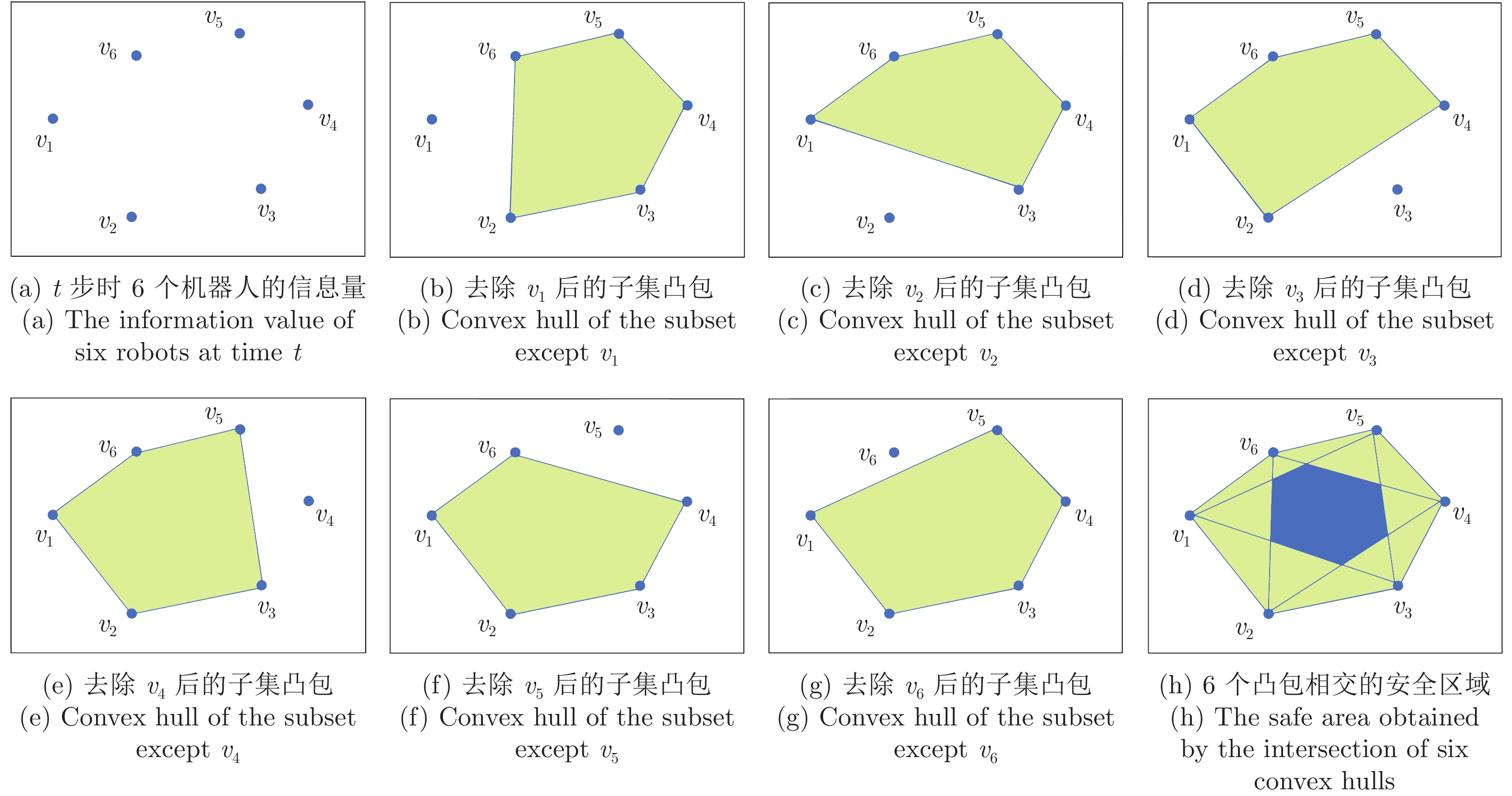
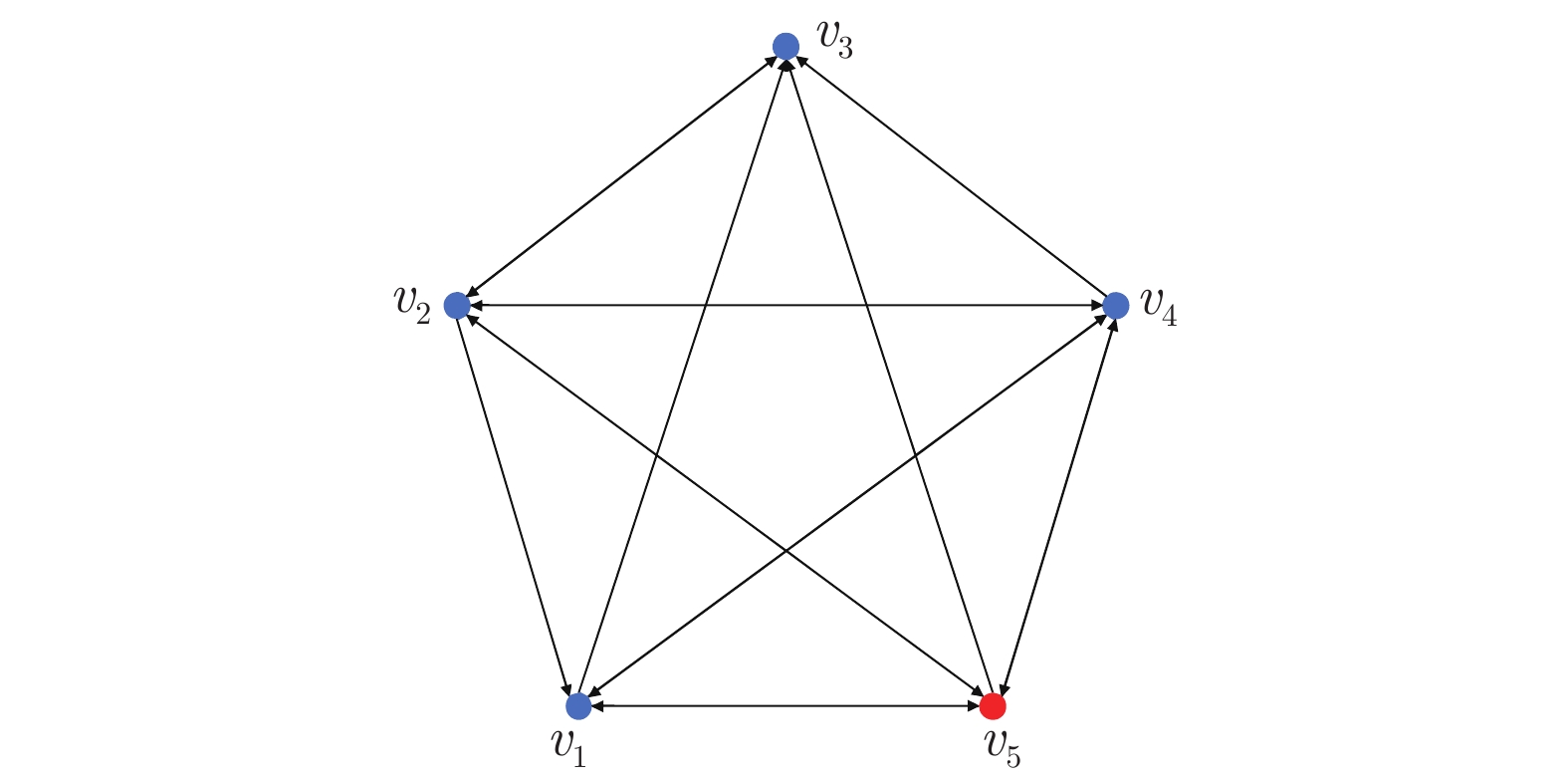
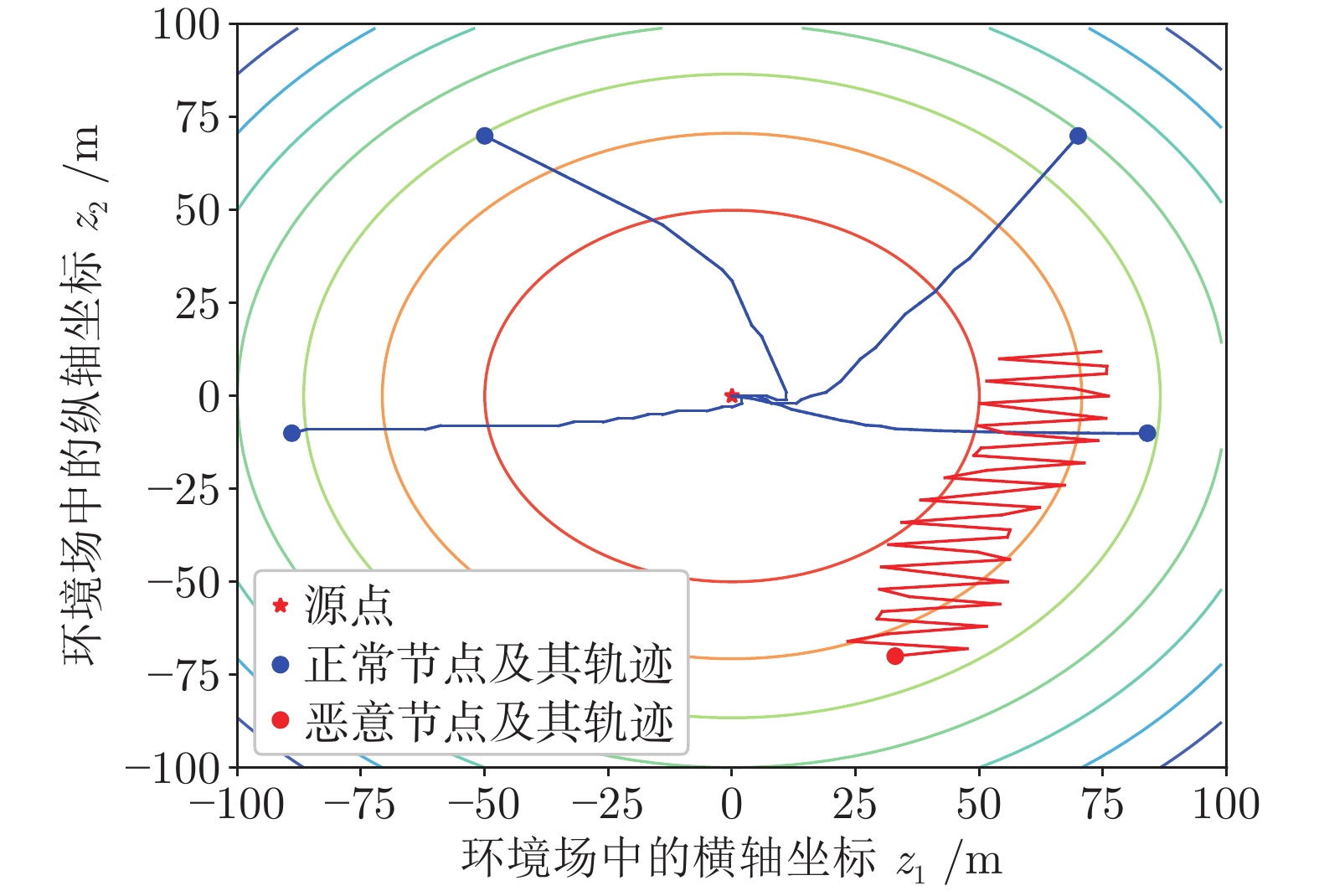
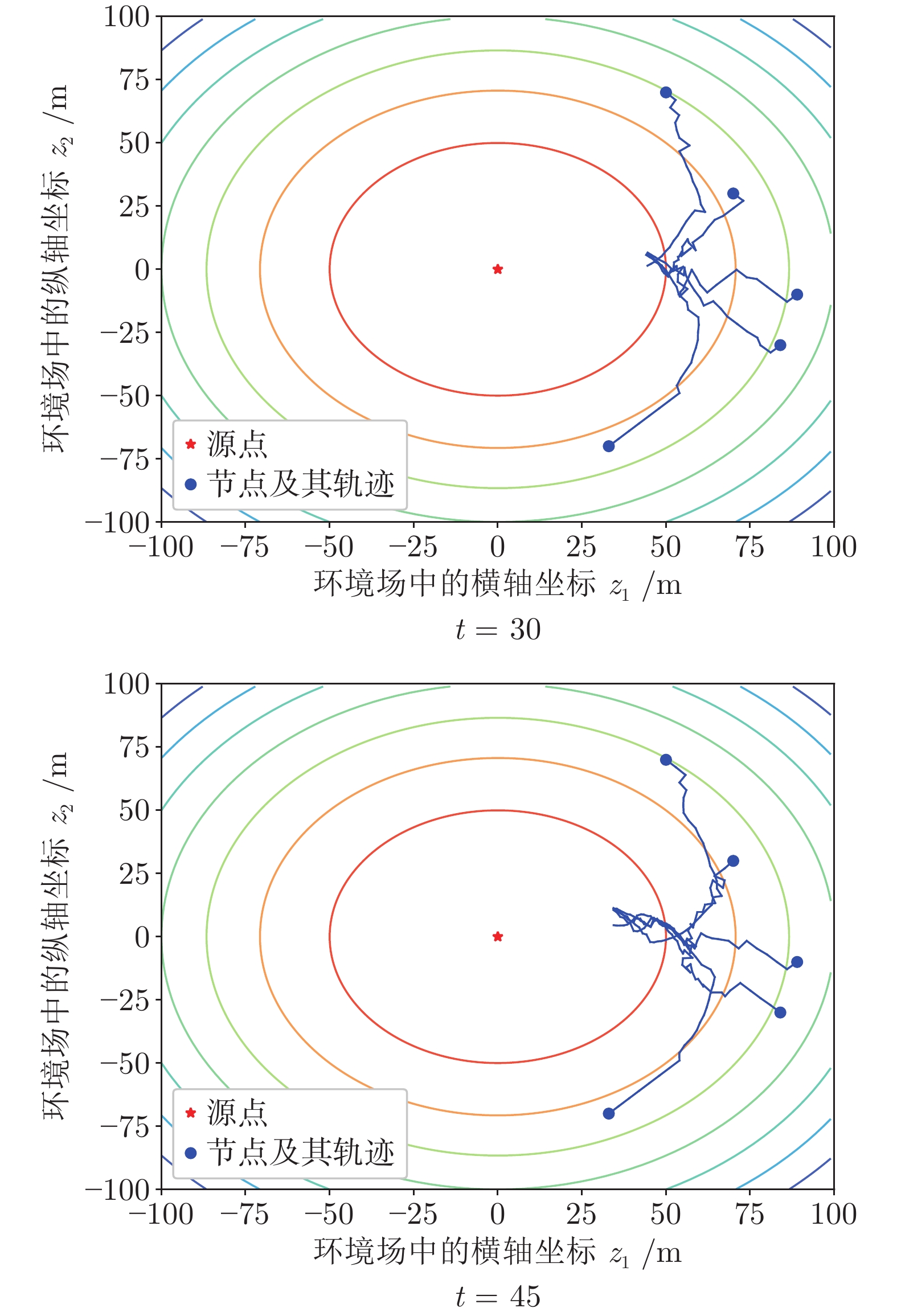
|
[1]
|
Turgeman A, Datar A, Werner H. Gradient free source-seeking using flocking behavior. In: Proceedings of the American Control Conference (ACC). Philadelphia, USA: IEEE, 2019. 4647−4652
|
|
[2]
|
孟庆浩, 李飞, 张明路, 曾明, 魏小博. 多自主体量化趋同与有限数据率趋同综述. 自动化学报, 2008, 34(10): 1281-1290Meng Qing-Hao, Li Fei, Zhang Ming-Lu, Zeng Ming, Wei Xiao-Bo. Study on realization method of multi-robot active olfaction in turbulent plum environments. Acta Automatica Sinica, 2008, 34(10): 1281-1290
|
|
[3]
|
Lu Q, Han Q L, Xie X G, Liu S R. A finite-time motion control strategy for odor source localization. IEEE Transactions on Industrial Electronics, 2014, 61(10): 5419-5430 doi: 10.1109/TIE.2014.2301751
|
|
[4]
|
李飞, 孟庆浩, 李吉功, 曾明. 基于P-PSO算法的室内有障碍通风环境下的多机器人气味源搜索. 自动化学报, 2009, 35(12): 1573-1579Li Fei, Meng Qing-Hao, Li Ji-Gong, Zeng Ming. P-PSO algorithm based multi-robot odor source search in ventilated indoor environment with obstacles. Acta Automatica Sinica, 2009, 35(12): 1573-1579
|
|
[5]
|
Shen X Y, Yuan J, Shan Y G. A novel plume tracking method in partial 3D diffusive environments using multi-sensor fusion. Expert Systems with Applications, 2021, 178: Article No. 114993 doi: 10.1016/j.eswa.2021.114993
|
|
[6]
|
Li Z, You K Y, Song S J. Cooperative source seeking via networked multi-vehicle systems. Automatica, 2020, 115: Article No. 108853 doi: 10.1016/j.automatica.2020.108853
|
|
[7]
|
Zou R, Kalivarapu V, Winer E, Oliver J, Bhattacharya S. Particle swarm optimization-based source seeking. IEEE Transactions on Automation Science and Engineering, 2015, 12(3): 865-875 doi: 10.1109/TASE.2015.2441746
|
|
[8]
|
张建化, 巩敦卫, 张勇. 基于微粒群优化的有限通信多机器人气味寻源. 控制与决策, 2013, 28(5): 726-730 doi: 10.13195/j.cd.2013.05.89.zhangjh.020Zhang Jian-Hua, Gong Dun-Wei, Zhang Yong. Localizing odor sources using multiple robots based on particle swarm optimization in limited communication environments. Control and Decision, 2013, 28(5): 726-730 doi: 10.13195/j.cd.2013.05.89.zhangjh.020
|
|
[9]
|
Moore B J, Canudas-de-Wit C. Source seeking via collaborative measurements by a circular formation of agents. In: Proceedings of the American Control Conference. Baltimore, USA: IEEE, 2010. 6417−6422
|
|
[10]
|
Fabbiano R, Garin F, Canudas-de-Wit C. Distributed source seeking without global position information. IEEE Transactions on Control of Network Systems, 2018, 5(1): 228-238 doi: 10.1109/TCNS.2016.2594493
|
|
[11]
|
Brinon-Arranz L, Schenato L. Consensus-based source-seeking with a circular formation of agents. In: Proceedings of the European Control Conference (ECC). Zurich, Switzerland: IEEE, 2013. 2831−2836
|
|
[12]
|
Xu Y, Deng G L, Zhang T W, Qiu H, Bao Y G. Novel denial-of-service attacks against cloud-based multi-robot systems. Information Sciences, 2021, 576: 329-344 doi: 10.1016/j.ins.2021.06.063
|
|
[13]
|
Zhou L F, Tzoumas V, Pappas G J, Tokekar P. Distributed attack-robust submodular maximization for multirobot planning. In: Proceedings of the IEEE International Conference on Robotics and Automation (ICRA). Paris, France: IEEE, 2020. 2479−2485
|
|
[14]
|
Deng G L, Zhou Y, Xu Y, Zhang T W, Liu Y. An investigation of Byzantine threats in multi-robot systems. In: Proceedings of the 24th International Symposium on Research in Attacks, Intrusions and Defenses. San Sebastian, Spain: ACM, 2021. 17−32
|
|
[15]
|
Fu W M, Qin J H, Zheng W X, Chen Y H, Kang Y. Resilient cooperative source seeking of double-integrator multi-robot systems under deception attacks. IEEE Transactions on Industrial Electronics, 2021, 68(5): 4218-4227 doi: 10.1109/TIE.2020.2987270
|
|
[16]
|
Vaidya N H, Garg V K. Byzantine vector consensus in complete graphs. In: Proceedings of the ACM Symposium on Principles of Distributed Computing. New York, USA: ACM, 2013. 65−73
|
|
[17]
|
Mendes H, Herlihy M. Multidimensional approximate agreement in Byzantine asynchronous systems. In: Proceedings of the 45th Annual ACM Symposium on Theory of Computing. New York, USA: ACM, 2013. 391−400
|
|
[18]
|
Abbas W, Shabbir M, Li J N, Koutsoukos X. Resilient distributed vector consensus using centerpoint. Automatica, 2022, 136: Article No. 110046 doi: 10.1016/j.automatica.2021.110046
|
|
[19]
|
Abbas W, Shabbir M, Li J N, Koutsoukos X. Interplay between resilience and accuracy in resilient vector consensus in multi-agent networks. In: Proceedings of the 59th IEEE Conference on Decision and Control (CDC). Jeju, South Korea: IEEE, 2020. 3127−3132
|
|
[20]
|
Vaidya N H. Iterative Byzantine vector consensus in incomplete graphs. arXiv preprint arXiv: 1307.2483, 2013.
|
|
[21]
|
Shabbir M, Li J N, Abbas W, Koutsoukos X. Resilient vector consensus in multi-agent networks using centerpoints. In: Proceedings of the American Control Conference (ACC). Denver, USA: IEEE, 2020. 4387−4392
|
|
[22]
|
Yan J Q, Li X X, Mo Y L, Wen C Y. Resilient multi-dimensional consensus in adversarial environment. arXiv preprint arXiv: 2001.00937, 2020.
|
|
[23]
|
Yan J Q, Mo Y L, Li X X, Xing L T, Wen C Y. Resilient vector consensus: An envent-based approach. In: Proceedings of the 16th International Conference on Control & Automation (ICCA). Singapore: IEEE, 2020. 889−894
|
|
[24]
|
Wang X, Mou S S, Sundaram S. A resilient convex combination for consensus-based distributed algorithms. arXiv preprint arXiv: 1806.10271, 2018.
|
|
[25]
|
Zhang H T, Sundaram S. Robustness of information diffusion algorithms to locally bounded adversaries. In: Proceedings of the American Control Conference (ACC). Montreal, Canada: IEEE, 2012. 5855−5861
|
|
[26]
|
Leblanc H J, Zhang H T, Koutsoukos X, Sundaram S. Resilient asymptotic consensus in robust networks. IEEE Journal on Selected Areas in Communications, 2013, 31(4): 766-781 doi: 10.1109/JSAC.2013.130413
|
|
[27]
|
Wu Y M, He X X. Secure consensus control for multi-agent systems with attacks and communication delays. IEEE/CAA Journal of Automatica Sinica, 2017, 4(1): 136-142 doi: 10.1109/JAS.2016.7510010
|




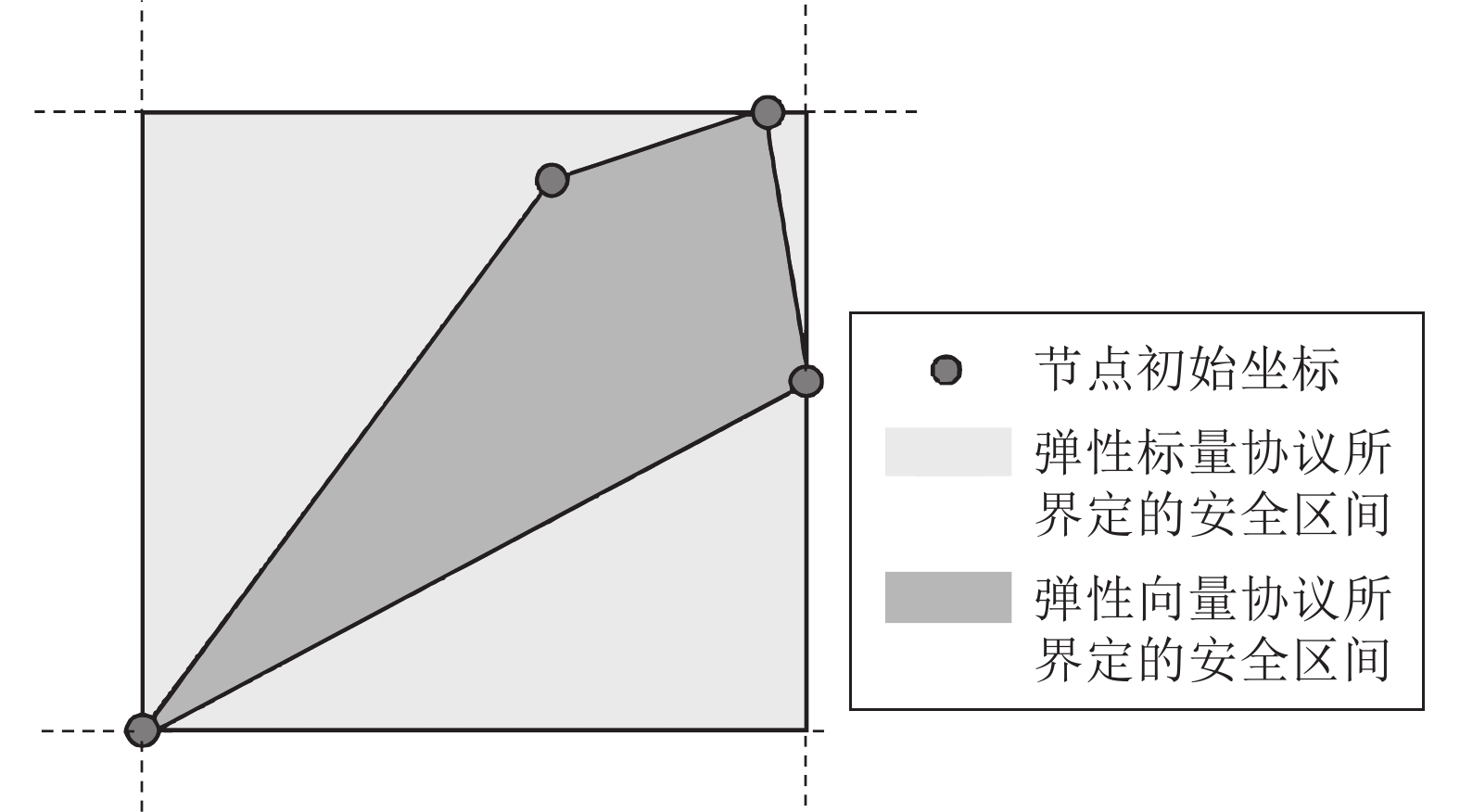
 下载:
下载: