-
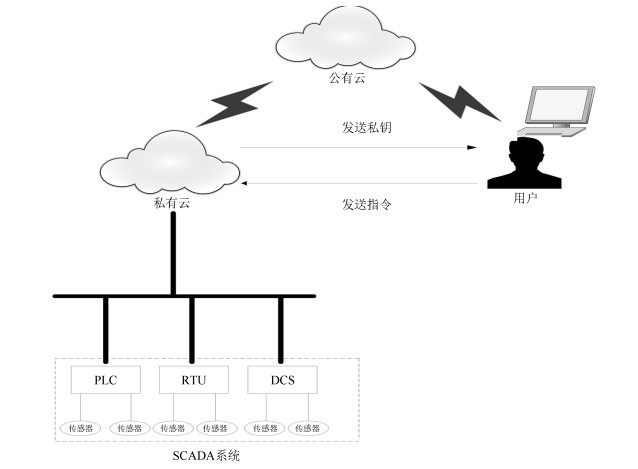
摘要: 随着云计算、物联网等信息通信技术与数据采集与监控系统的整合, 工业控制系统面临新的安全问题, 其中数据的完整性、机密性保护和有效的身份认证问题受到了关注.为了在这样一个多功能、分布式的环境中解决这些问题, 该文利用基于属性的加密方法, 构建访问控制策略, 为用户提供身份认证和授权服务, 保护用户与工业控制系统间的数据通信安全并实时检查存储数据的完整性.方案从正确性、安全性及系统性能等方面做出分析, 并与常用的认证方法进行了对比.Abstract: With the integration of cloud computing, internet of things (IoT) and supervisory control and data acquisition (SCADA) system, industrial control system (ICS) is faced with new security issues. Among them, the issue of data integrity, confidentiality protection and effective authentication has drawn attention. To address these issues in such a versatile and distributed environment, attribute-based encryption is used to construct access control policies, provide authentication and authorization services, protect the data communication between users and ICS and check the integrity of stored data in real time. We prove the correctness of the scheme, analyze its security and evaluate its performance, also compare it with the commonly used methods.
-
Key words:
- Industrial control system /
- access control /
- authentication /
- integrity /
- confidentiality
1) 本文责任编委 李乐飞 -
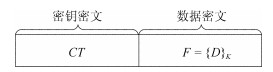
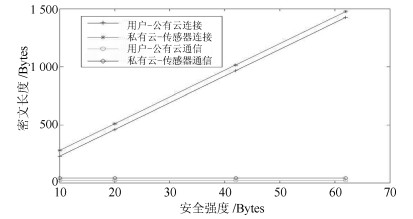
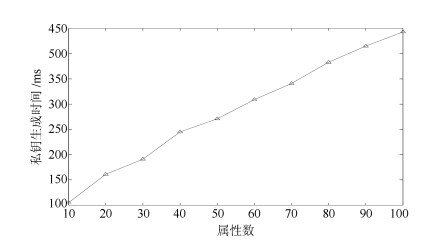
表 1 密文长度
Table 1 Length of ciphertext
实体之间 加密(Byte) 解密 用户-公有云建立连接 22$\left| p\right|$ 1 用户-公有云数据传输 16 1 用户-私有云建立连接 22$\left| p\right|$+16 1 用户-私有云数据传输 34 1 表 2 计算开销
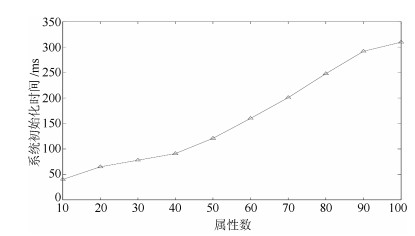
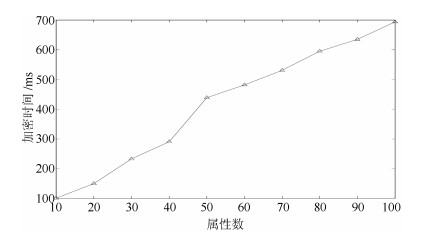
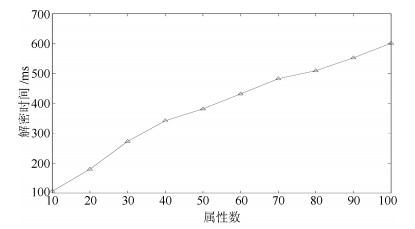
Table 2 Computation overhead
方案 计算开销(ms) 基于证书的认证 36.96$N$ 基于默克尔树的认证 18.48$N$ 基于身份的认证 124.08$N$ 数据用户与公有云或私有云的通信 1 364.88$N$ -
[1] Sajid A, Abbas H, Saleem K. Cloud-assisted IoT-based SCADA systems security: A review of the state of the art and future challenges. IEEE Access, 2016, 4: 1375-1384 doi: 10.1109/ACCESS.2016.2549047 [2] Langmann R, Rojas-Peña L F. A PLC as an industry 4.0 component. In: Proceedings of the 13th International Conference on Remote Engineering and Virtual Instrumentation (REV). Madrid, Spain: IEEE, 2016. 10-15 [3] Wan J F, Tang S L, Shu Z G, Li D, Wang S Y, Imran M, et al. Software-defined industrial internet of things in the context of industry 4.0. IEEE Sensors Journal, 2016, 16(20): 7373-7380 [4] Goldin E, Feldman D, Georgoulas G, Castano M, Nikolakopoulos G. Cloud computing for big data analytics in the process control industry. In: Proceedings of the 25th Mediterranean Conference on Control and Automation (MED). Valletta, Malta: IEEE, 2017. 1373-1378 [5] 夏元清.云控制系统及其面临的挑战.自动化学报, 2016, 42(1): 1-12 doi: 10.3969/j.issn.1003-8930.2016.01.001Xia Yuan-Qing. Cloud control systems and their challenges. Acta Automatica Sinica, 2016, 42(1): 1-12 doi: 10.3969/j.issn.1003-8930.2016.01.001 [6] Farwell J P, Rohozinski R. Stuxnet and the future of cyber war. Survival, 2011, 53(1): 23-40 doi: 10.1080/00396338.2011.555586 [7] 周小峰, 陈秀真.面向工业控制系统的灰色层次信息安全评估模型.信息网络安全, 2014, (1): 15-20 https://www.cnki.com.cn/Article/CJFDTOTAL-XXAQ201401006.htmZhou Xiao-Feng, Chen Xiu-Zhen. Gray analytical hierarchical assessment model for industry control system security. Netinfo Security, 2014, (1): 15-20 https://www.cnki.com.cn/Article/CJFDTOTAL-XXAQ201401006.htm [8] Singh A, Prasad A, Talwar Y. SCADA security issues and FPGA implementation of AES—A review. In: Proceedings of the 2nd International Conference on Next Generation Computing Technologies (NGCT). Dehradun, India: IEEE, 2016. 899-904 [9] 梁耀, 冯冬芹, 徐珊珊, 陈思媛, 高梦州.加密传输在工控系统安全中的可行性研究.自动化学报, 2018, 44(3): 434-442 doi: 10.16383/j.aas.2018.c160399Liang Yao, Feng Dong-Qin, Xu Shan-Shan, Chen Si-Yuan, Gao Meng-Zhou. Feasibility analysis of encrypted transmission on security of industrial control systems. Acta Automatica Sinica, 2018, 44(3): 434-442 doi: 10.16383/j.aas.2018.c160399 [10] Zhou X J, Xu Z, Wang L M, Chen K. What should we do? A structured review of scada system cyber security standards. In: Proceedings of the 4th International Conference on Control, Decision and Information Technologies (CoDIT). Barcelona, Spain: IEEE, 2017. 605-614 [11] 陆耿虹, 冯冬芹.基于粒子滤波的工业控制网络态势感知建模.自动化学报, 2018, 44(8): 1405-1412 doi: 10.16383/j.aas.2017.c160830Lu Geng-Hong, Feng Dong-Qin. Modeling of the industrial control network situation awareness based on particle Filtering. Acta Automatica Sinica, 2018, 44(8): 1405-1412 doi: 10.16383/j.aas.2017.c160830 [12] Shahzad A, Musa S, Aborujilah A, Irfan M. Industrial control systems (ICSs) vulnerabilities analysis and SCADA security enhancement using testbed encryption. In: Proceedings of the 8th International Conference on Ubiquitous Information Management and Communication. Siem Reap, Cambodia: Elsevier, 2014. 1-7 [13] Oualha N, Olivereau A, Boudguiga A. Pseudonymous communications in secure industrial wireless sensor networks. In: Proceedings of the 11th Annual Conference on Privacy, Security and Trust. Tarragona, Spain: IEEE, 2013. 98-102 [14] Halas M, Bestak I, Orgon M, Kovac A. Performance measurement of encryption algorithms and their effect on real running in PLC networks. In: Proceedings of the 35th International Conference on Telecommunications and Signal Processing (TSP). Prague, Czech Republic: IEEE, 2012. 161-164 [15] Bere M, Muyingi H. Initial investigation of industrial control system (ICS) security using artificial immune system (AIS). In: Proceedings of the 2015 International Conference on Emerging Trends in Networks and Computer Communications (ETNCC). Windhoek, Namibia: IEEE, 2015. 79-84 [16] Morrow B. BYOD security challenges: control and protect your most sensitive data. Network Security, 2012, 2012(12): 5-8 doi: 10.1016/S1353-4858(12)70111-3 [17] Cazorla L, Alcaraz C, Lopez J. Cyber stealth attacks in critical information infrastructures. IEEE Systems Journal, 2018, 12(2): 1778-1792 doi: 10.1109/JSYST.2015.2487684 [18] Jenkins J, Burmester M. Protecting infrastructure assets from real-time and run-time threats. In: Proceedings of the 7th International Conference on Critical Infrastructure Protection Ⅶ. Washington, USA: Springer, 2013. 97-110 [19] 丁心志, 李慧杰, 杨慧霞, 张喜玲, 刘柱揆.基于IEC/TC57国际标准体系现状分析研究与展望.电力系统保护与控制, 2014, 42(21): 145-154 doi: 10.7667/j.issn.1674-3415.2014.21.023Ding Xin-Zhi, Li Hui-Jie, Yang Hui-Xia, Zhang Xi-Ling, Liu Zhu-Kui. Present situation analysis and prospect for international standards system based on IEC/TC 57. Power System Protection and Control, 2014, 42(21): 145-154 doi: 10.7667/j.issn.1674-3415.2014.21.023 [20] Sandhu R S, Coyne E J, Feinstein H L, Youman C E. Role-based access control models. Computer, 1996, 29(2): 38-47 doi: 10.1109/2.485845 [21] Soni A, Keoh S L, Kumar S S, Garcia-Morchon O. Hada: hybrid access decision architecture for building automation and control systems. In: Proceedings of the 1st International Symposium on ICS & SCADA Cyber Security Research 2013. Swindon, UK: BCS, 2013. 1-11 [22] 张婷, 杨庚, 滕玮, 王东阳.云计算中基于属性和定长密文的访问控制方法.计算机技术与发展, 2013, 23(11): 128-132 https://www.cnki.com.cn/Article/CJFDTOTAL-WJFZ201311033.htmZhang Ting, Yang Geng, Teng Wei, Wang Dong-Yang. Access control method based on attribute and constant-size ciphertext in cloud computing. Computer Technology and Development, 2013, 23(11): 128-132 https://www.cnki.com.cn/Article/CJFDTOTAL-WJFZ201311033.htm [23] 冯登国, 陈成.属性密码学研究.密码学报, 2014, 1(1): 1-12 https://www.cnki.com.cn/Article/CJFDTOTAL-MMXB201401004.htmFeng Deng-Guo, Chen Cheng. Research on attribute-based cryptography. Journal of Cryptologic Research, 2014, 1(1): 1-12 https://www.cnki.com.cn/Article/CJFDTOTAL-MMXB201401004.htm [24] Yu S C, Wang C, Ren K, Lou W J. Attribute based data sharing with attribute revocation. In: Proceedings of the 5th ACM Symposium on Information, Computer and Communications Security. Beijing, China: IEEE, 2010. 261-270 [25] Zu L H, Liu Z H, Li J J. New ciphertext-policy attribute-based encryption with efficient revocation. In: Proceedings of the 4th International Conference on Computer and Information Technology. Xi'an, China: IEEE, 2014. 281-287 [26] Colbert E J M, Kott A. Cyber-Security of SCADA and Other Industrial Control Systems. Switzerland: Springer International Publishing, 2016. [27] Hu C Q, Li H J, Huo Y, Xiang T, Liao X F. Secure and efficient data communication protocol for wireless body area networks. IEEE Transactions on Multi-Scale Computing Systems, 2016, 2(2): 94-107 doi: 10.1109/TMSCS.2016.2525997 -




 下载:
下载: