-
摘要: 为了解决传统鲁棒水印技术不可感知性和鲁棒性间的矛盾,对空域零水印技术进行研究,分析了常规图像处理攻击对载体图像所有选择分块整体均值与分块均值间大小关系的影响,结果表明此关系具有较强的稳健性.基于此,提出了一种新的空域强鲁棒零水印方案.1)利用混沌系统对初值敏感的特性映射图像分块的位置和采用混沌加密与Arnold空间置乱技术对原始水印信号进行预处理;2)采用载体图像所有选择分块整体均值与分块均值间大小关系的稳健性能来构造特征信息;3)采用混沌加密和Arnold空间置乱技术对生成的零水印信号进行后处理.仿真实验结果表明,本文算法对常规的图像处理、尺寸缩放、旋转和多种组合攻击等都表现出较强的抗攻击能力.与相似的鲁棒零水印方案相比,本文算法的平均运行时间不仅减少了约90%,而且抗攻击平均性能提高了约15%,表明它具有较低的计算复杂度和更优越的鲁棒性能,适用于对载体图像质量要求较高的作品版权保护应用场合.Abstract: In order to solve the contradiction between imperceptibility and robustness of traditional robust watermarking technology, the spatial domain zero watermarking technology is researched and the effect of the numerical relationship between the overall mean of all selected blocks and block mean against common image processing attacks is analyzed. The results show that the numerical relationship has strong stability. Based on this, a new zero watermarking scheme with strong robustness in the spatial domain is proposed. Firstly, using the characteristic of sensitivity to initial value, logistic mapping is used to find the position of image block and the original copyright information is pre-processed by chaotic encryption and Arnold scrambling technologies. Secondly, the stability of the numerical relationship between the overall mean of all selected blocks and block mean is utilized to generate feature information. Finally, the generated zero watermarking signal is post-processed again by chaotic encryption and Arnold scrambling technologies. Experimental results on a large number of standard test images show that the proposed algorithm has strong robustness against common image processing, scaling, rotation, and various combination attacks. Compared with similar robust zero watermarking schemes, the proposed scheme not only saves 90% running time but also improves robustness performance by 15% on average. These results show that it has lower computational complexity and better performance and can be applied in copyright protection applications for high quality requirements of cover images.
-
Key words:
- Chaos system /
- spatial domain /
- zero watermarking /
- common attack /
- combination attack /
- robustness
1) 本文责任编委 赖剑煌 -
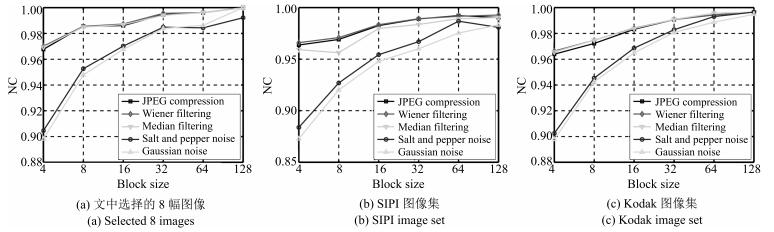
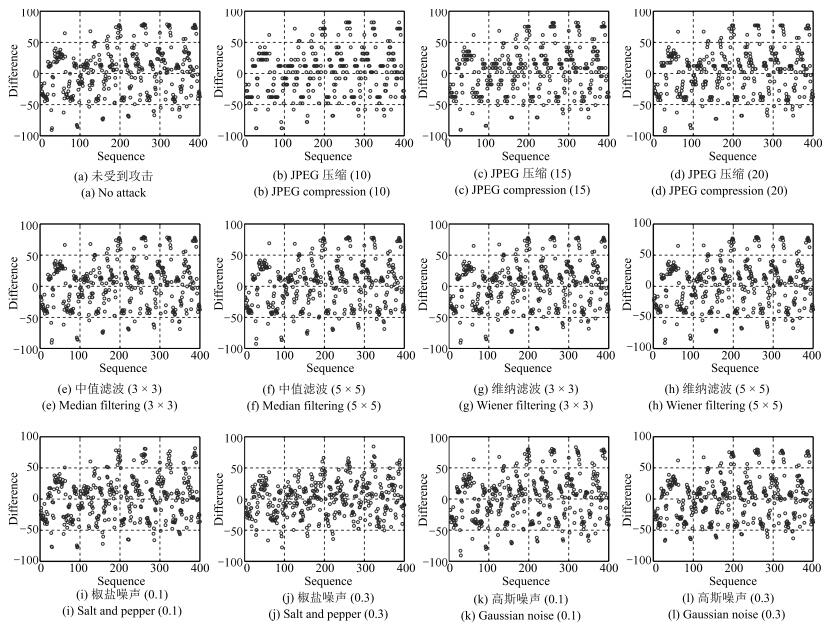
表 1 所有选择分块整体均值与分块均值间差值关系变化情况(%)
Table 1 The changes of difference relationship between the overall mean of all selected blocks and block mean (%)
图像集 攻击方式 $P_{1}$ $P_{2}$ $P_{3}$ $P_{4}$ JPEG压缩(20) 2.5417 0.8506 21.1772 中值滤波(3 × 3) 2.7067 0.7202 21.0870 Kodak 维纳滤波(3 × 3) 2.6860 0.7406 21.0334 21.0992 椒盐噪声(0.1) 10.6074 2.7533 22.5952 高斯噪声(0.1) 13.5641 3.1607 22.6128 JPEG压缩(20) 3.3064 2.6867 33.8072 中值滤波(3 × 3) 3.3476 2.4786 33.8938 SIPI 维纳滤波(3 × 3) 3.1466 2.4220 33.6135 34.2121 椒盐噪声(0.1) 12.0245 9.9359 35.5716 高斯噪声(0.1) 13.6321 11.8315 35.8746 JPEG压缩(20) 3.0059 0.4684 12.9183 中值滤波(3 × 3) 3.2848 0.4411 12.8613 UCID 维纳滤波(3 × 3) 2.9985 0.3996 12.8779 12.9180 椒盐噪声(0.1) 13.4309 1.5459 14.1185 高斯噪声(0.1) 19.5050 1.7995 14.3138 表 2 组合攻击
Table 2 Combination attacks
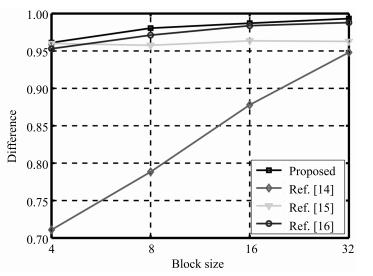
JPEG压缩 中值滤波 维纳滤波 椒盐噪声 高斯噪声 攻击方式1 20 3 × 3 3 × 3 0.1 0.1 攻击方式2 15 5 × 5 5 × 5 0.2 0.2 攻击方式3 10 7 × 7 7 × 7 0.3 0.3 表 3 在给定阈值条件下, 所有选择分块整体均值与分块均值间差值关系变化情况(%)
Table 3 The changes of difference relationship between the overall mean of all selected blocks and block mean with a given threshold (%)
图像集 阈值$T$ 攻击方式 $P_{1}$ $P_{2}$ $P_{3}$ $P_{4}$ Kodak 10 攻击方式1 6.3325 1.6419 21.7064 攻击方式2 12.2779 3.1058 21.0334 22.4345 攻击方式3 22.4367 4.8887 23.4951 20 攻击方式1 5.4244 2.8775 39.5189 攻击方式2 11.9098 6.1418 38.2100 41.3628 攻击方式3 21.6383 10.0186 43.5223 SIPI 10 攻击方式1 7.0620 5.8494 34.6629 攻击方式2 14.6056 10.5559 33.6135 36.0441 攻击方式3 25.8649 16.0384 38.2140 20 攻击方式1 4.7413 6.2570 59.5355 攻击方式2 10.2979 12.7624 58.0793 61.7652 攻击方式3 17.4728 20.5366 64.3733 UCID 10 攻击方式1 8.5528 0.9181 13.4140 攻击方式2 19.8770 1.9943 12.8779 14.1996 攻击方式3 39.3653 3.7169 15.6343 20 攻击方式1 8.1239 2.1013 26.2574 攻击方式2 18.2561 4.6279 25.0641 27.9303 攻击方式3 33.9565 8.3950 30.4609 表 4 不同载体图像生成的特征信息和零水印均衡性测试
Table 4 Balance test of generated feature information and zero watermarking from different cover images
特征信息$B$ 最终生成的零水印 $N_{0}$ $N_{1}$ $E$ $N_{0}$ $N_{1}$ $E$ Aerial 1 652 2 444 0.1934 2 055 2 041 0.0034 Barbara 2 083 2 013 0.0171 2 086 2 010 0.0186 Boat 1 366 2 730 0.3330 2 055 2 041 0.0034 Couple 1 825 2 271 0.1089 1 998 2 098 0.0244 Elain 2 088 2 008 0.0195 2 085 2 011 0.0181 Frog 2 027 2 069 0.0103 2 042 2 054 0.0029 Goldhill 2 226 1 870 0.0869 2 005 2 091 0.0210 Zelda 1 943 2 153 0.0513 2 078 2 018 0.0146 平均值 1 901 2 195 0.1026 2 051 2 046 0.0133 表 5 不同算法生成的特征信息和零水印均衡性测试
Table 5 Balance test of generated feature information and zero watermarking from different algorithms
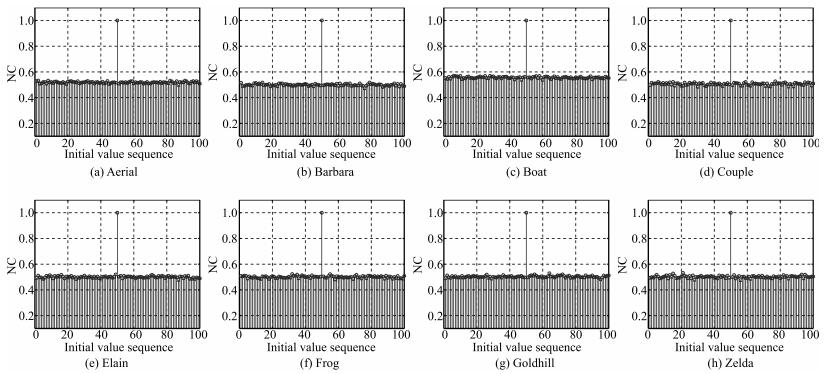
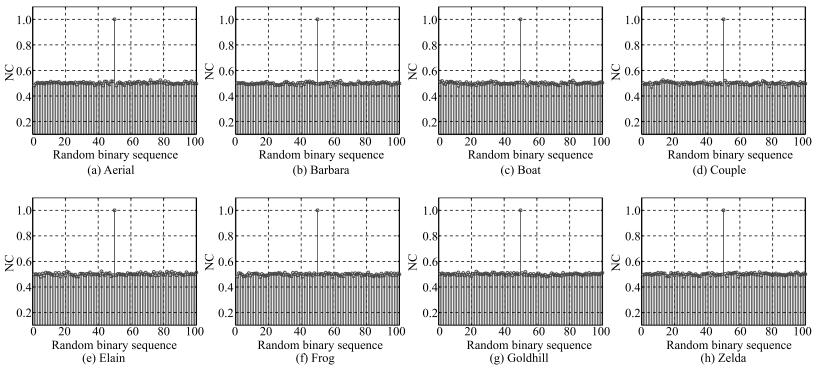
表 6 不同载体图像零水印间的相似度
Table 6 Similarities between the generated zero watermarking from different cover images
Aerial Barbara Boat Couple Elain Frog Goldhill Zelda Aerial 1.0000 0.5149 0.5498 0.4900 0.4810 0.4651 0.5513 0.5344 Barbara 0.5149 1.0000 0.5330 0.4878 0.5300 0.4897 0.4944 0.4850 Boat 0.5498 0.5330 1.0000 0.5881 0.4756 0.4734 0.5894 0.4465 Couple 0.4900 0.4878 0.5881 1.0000 0.4880 0.4951 0.5461 0.4292 Elain 0.4810 0.5300 0.4756 0.4880 1.0000 0.4832 0.5659 0.5051 Frog 0.4651 0.4897 0.4734 0.4951 0.4832 1.0000 0.4890 0.4912 Goldhill 0.5513 0.4944 0.5894 0.5461 0.5659 0.4890 1.0000 0.5002 Zelda 0.5344 0.4850 0.4465 0.4292 0.5051 0.4912 0.5002 1.0000 表 7 不同算法零水印间的相似度
Table 7 Similarities between the generated zero watermarking from different algorithms
表 8 抗噪声攻击实验结果
Table 8 Experimental results against noise attacks
攻击
方式噪声
强度PSNR NC 本文 [13] [14] [15] [16] 椒盐
噪声0.1 15.3992 0.9510 0.6901 0.6318 0.7859 0.8789 0.2 12.3662 0.9239 0.6235 0.5754 0.7461 0.8213 0.3 10.6169 0.8932 0.5927 0.5458 0.7316 0.7741 0.4 9.3830 0.8640 0.5718 0.5292 0.7040 0.7347 0.5 8.4076 0.8289 0.5594 0.5139 0.6700 0.6960 平均值 11.2345 0.8922 0.6075 0.5592 0.7275 0.7810 高斯
噪声0.1 17.1752 0.9756 0.7915 0.7084 0.8910 0.9298 0.2 13.3711 0.9712 0.7885 0.7094 0.8769 0.9263 0.3 10.6398 0.9550 0.7893 0.7016 0.8271 0.9207 0.4 8.7613 0.9241 0.7731 0.6821 0.7332 0.9067 0.5 7.4853 0.8804 0.7500 0.6617 0.6197 0.8783 平均值 11.4865 0.9413 0.7785 0.6927 0.7896 0.9124 表 9 抗滤波攻击实验结果
Table 9 Experimental results against filtering attacks
攻击
方式窗口
大小PSNR NC 本文 [13] [14] [15] [16] 中值
滤波3 × 3 30.0745 0.9922 0.9132 0.9006 0.9678 0.9816 5 × 5 27.4016 0.9846 0.8826 0.8505 0.9503 0.9650 7 × 7 26.1452 0.9754 0.8652 0.8089 0.9353 0.9482 9 × 9 25.1367 0.9669 0.8495 0.7746 0.9226 0.9335 11 × 11 24.3752 0.9590 0.8348 0.7429 0.9106 0.9207 平均值 26.6266 0.9756 0.8691 0.8155 0.9373 0.9498 维纳
滤波3 × 3 33.3994 0.9959 0.9417 0.9211 0.9733 0.9878 5 × 5 30.7947 0.9915 0.9237 0.8762 0.9600 0.9745 7 × 7 29.3403 0.9855 0.9094 0.8373 0.9469 0.9598 9 × 9 28.2680 0.9790 0.8965 0.8062 0.9335 0.9455 11 × 11 27.4357 0.9710 0.8876 0.7792 0.9228 0.9346 平均值 29.8476 0.9846 0.9118 0.8440 0.9473 0.9605 表 10 抗JPEG压缩攻击实验结果
Table 10 Experimental results against JPEG compression attacks
品质百分数
(%)PSNR NC 本文 [13] [14] [15] [16] 5 25.5419 0.9559 0.8640 0.6803 0.8941 0.9054 10 27.9958 0.9856 0.8998 0.7787 0.9364 0.9513 15 29.3245 0.9837 0.9138 0.8188 0.9498 0.9661 20 30.2552 0.9866 0.9227 0.8468 0.9571 0.9727 25 30.9669 0.9861 0.9274 0.8721 0.9607 0.9780 30 31.5407 0.9955 0.9317 0.8845 0.9651 0.9813 35 32.0416 0.9932 0.9358 0.8966 0.9656 0.9835 40 32.4319 0.9922 0.9381 0.9019 0.9680 0.9864 45 32.8186 0.9941 0.9424 0.9135 0.9688 0.9870 50 33.1562 0.9952 0.9431 0.9221 0.9706 0.9879 平均值 30.6073 0.9868 0.9219 0.8515 0.9536 0.9700 表 11 抗常规图像处理组合攻击实验结果
Table 11 Experimental results against common image processing combination attacks
攻击方式 PSNR NC 本文 [13] [14] [15] [16] 中值滤波(5 × 5) +椒盐噪声(0.3) 10.5309 0.8901 0.5784 0.5299 0.7235 0.7685 中值滤波(5 × 5) +高斯噪声(0.3) 10.4693 0.9501 0.7434 0.6449 0.8141 0.9107 维纳滤波(5 × 5) +椒盐噪声(0.3) 10.5801 0.8926 0.5836 0.5341 0.7244 0.7699 维纳滤波(5 × 5) +高斯噪声(0.3) 10.5371 0.9566 0.7641 0.6583 0.8242 0.9139 中值滤波(5 × 5) + JPEG压缩(10) 26.1020 0.9762 0.8676 0.7212 0.9219 0.9341 维纳滤波(5 × 5) + JPEG压缩(10) 27.1870 0.9819 0.8835 0.7425 0.9264 0.9429 JPEG压缩(10) +椒盐噪声(0.3) 10.5540 0.8929 0.5866 0.5481 0.7268 0.7714 JPEG压缩(10) +高斯噪声(0.3) 10.5560 0.9551 0.7610 0.6920 0.8228 0.9099 JPEG压缩(10) +放大2倍+缩小0.5倍 28.3582 0.9856 0.9039 0.8112 0.9417 0.9555 逆时针旋转2度+ JPEG压缩(10) 17.6329 0.8628 0.6854 0.6457 0.8010 0.8060 平均值 18.8576 0.9356 0.7641 0.6879 0.8438 0.8772 表 12 抗偏移行列攻击实验结果
Table 12 Experimental results against row and column shifting attacks
攻击方式 PSNR NC 本文 [13] [14] [15] [16] 右偏移2列 21.2879 0.9489 0.7796 0.8425 0.9056 0.9129 左偏移2列 21.4324 0.9497 0.7831 0.8425 0.9068 0.9118 上偏移2行 21.9757 0.9522 0.7966 0.8473 0.9172 0.9237 下偏移2行 21.6893 0.9504 0.7897 0.8445 0.9104 0.9198 右偏移2列+上偏移2行 19.8069 0.9271 0.7444 0.7919 0.8827 0.8882 左偏移2列+上偏移2行 19.8413 0.9220 0.7468 0.7906 0.8792 0.8862 右偏移2列+下偏移2行 19.5717 0.9239 0.7410 0.7882 0.8728 0.8807 左偏移2列+下偏移2行 19.7364 0.9248 0.7423 0.7910 0.8747 0.8837 平均值 20.1291 0.9296 0.7528 0.8012 0.8840 0.8917 表 13 抗偏移行列组合攻击实验结果
Table 13 Experimental results against row and column shifting combination attacks
攻击方式 PSNR NC 本文 [13] [14] [15] [16] 右偏移2列+上偏移2行+逆时针旋转2度 17.1498 0.8561 0.6787 0.6987 0.8225 0.8287 左偏移2列+上偏移2行+逆时针旋转2度 17.1585 0.8554 0.6760 0.7019 0.7764 0.7808 右偏移2列+下偏移2行+放大2倍+缩放0.5倍 19.9653 0.9242 0.7479 0.7871 0.8733 0.8811 左偏移2列+下偏移2行+缩放0.5倍+放大2倍 20.9519 0.9254 0.7674 0.7762 0.8727 0.8839 平均值 18.8166 0.8993 0.7268 0.7304 0.8378 0.8503 表 14 抗缩放攻击实验结果
Table 14 Experimental results against scaling attacks
插值方法 攻击方式 PSNR NC 本文 [13] [14] [15] [16] bilinear 缩小0.25倍+放大4倍 25.4763 0.9786 0.8584 0.8108 0.9246 0.9475 缩小0.5倍+放大2倍 28.3491 0.9917 0.8994 0.8825 0.9492 0.9735 放大4倍+缩小0.25倍 34.2862 0.9976 0.9483 0.9454 0.9742 0.9898 放大2倍+缩小0.5倍 33.5935 0.9972 0.9433 0.9397 0.9725 0.9891 bicubic 缩小0.25倍+放大4倍 26.4544 0.9910 0.8710 0.8348 0.9399 0.9663 缩小0.5倍+放大2倍 29.9015 0.9968 0.9129 0.9123 0.9626 0.9875 放大4倍+缩小0.25倍 39.3801 0.9989 0.9710 0.9699 0.9859 0.9954 放大2倍+缩小0.5倍 39.0522 0.9987 0.9702 0.9671 0.9855 0.9950 nearest 缩小0.25倍+放大4倍 23.1304 0.9564 0.8201 0.6959 0.9019 0.9089 缩小0.5倍+放大2倍 25.6881 0.9790 0.8653 0.8456 0.9430 0.9522 放大4倍+缩小0.25倍 +$\infty $ 1.0000 1.0000 1.0000 1.0000 1.0000 放大2倍+缩小0.5倍 +$\infty $ 1.0000 1.0000 1.0000 1.0000 1.0000 平均值 30.5312 0.9905 0.9217 0.9003 0.9616 0.9754 表 15 抗仅缩小或放大缩放攻击实验结果
Table 15 Experimental results against only reduce/enlarge scaling attacks
插值方法 攻击方式 NC 本文 [13] [14] [15] [16] bilinear 缩小0.5倍 0.9963 0.6365 0.9079 0.9587 0.9856 缩小2倍 0.9982 0.7503 0.9607 0.9818 0.9925 放大4倍 0.9982 0.5657 0.9651 0.9837 0.9928 bicubic 缩小0.5倍 0.9976 0.6371 0.9202 0.9643 0.9896 放大2倍 0.9989 0.7507 0.9795 0.9914 0.9965 放大4倍 0.9988 0.5658 0.9791 0.9906 0.9960 nearest 缩小0.5倍 0.9790 0.6202 0.8456 0.9432 0.9522 放大2倍 1.0000 0.7513 1.0000 1.0000 1.0000 放大4倍 1.0000 0.5693 0.9999 1.0000 1.0000 平均值 0.9963 0.6497 0.9509 0.9793 0.9895 表 16 抗旋转攻击实验结果
Table 16 Experimental results against rotation attacks
插值
方法攻击
方式PSNR NC 本文 [13] [14] [15] [16] bilinear 1° 20.0928 0.9209 0.7514 0.7812 0.8750 0.8809 -1° 20.2172 0.9216 0.7476 0.7753 0.8781 0.8812 3° 16.1739 0.8209 0.6407 0.6640 0.7670 0.7680 -3° 16.3061 0.8223 0.6172 0.6645 0.7720 0.7713 5° 14.5964 0.7571 0.5945 0.6242 0.7097 0.7081 -5° 14.7210 0.7607 0.5645 0.6264 0.7191 0.7177 10° 12.8664 0.6633 0.5369 0.5844 0.6292 0.6315 -10° 12.9698 0.6709 0.5140 0.5825 0.6436 0.6416 30° 10.8797 0.5582 0.4880 0.5235 0.5487 0.5541 -30° 10.9389 0.5634 0.5093 0.5236 0.5525 0.5489 bicubic 1° 19.8760 0.9208 0.7466 0.7815 0.8739 0.8797 -1° 19.9959 0.9211 0.7437 0.7773 0.8776 0.8802 3° 16.0703 0.8205 0.6376 0.6664 0.7655 0.7672 -3° 16.1995 0.8221 0.6147 0.6667 0.7710 0.7702 5° 14.5213 0.7573 0.5934 0.6247 0.7083 0.7072 -5° 14.6440 0.7610 0.5623 0.6280 0.7190 0.7171 10° 12.8152 0.6631 0.5359 0.5847 0.6290 0.6313 -10° 12.9175 0.6708 0.5147 0.5847 0.6434 0.6410 30° 10.8483 0.5582 0.4877 0.5245 0.5488 0.5538 -30° 10.9075 0.5630 0.5083 0.5239 0.5520 0.5491 nearest 1° 19.6571 0.9211 0.7445 0.7818 0.8752 0.8796 -1° 19.7749 0.9214 0.7403 0.7780 0.8779 0.8821 3° 15.9727 0.8203 0.6365 0.6663 0.7640 0.7680 -3° 16.0995 0.8221 0.6150 0.6668 0.7713 0.7717 5° 14.4531 0.7569 0.5928 0.6267 0.7071 0.7080 -5° 14.5743 0.7610 0.5625 0.6247 0.7180 0.7171 10° 12.7704 0.6636 0.5345 0.5843 0.6281 0.6309 -10° 12.8715 0.6705 0.5141 0.5836 0.6425 0.6421 30° 10.8207 0.5579 0.4895 0.5212 0.5493 0.5539 -30° 10.8800 0.5634 0.5089 0.5224 0.5530 0.5486 平均值 14.8811 0.7458 0.5949 0.6356 0.7090 0.7101 表 17 本文算法与其他算法抗攻击性能的提高率(%)
Table 17 Improvement performance against attacks compared this algorithm with other algorithms (%)
表 18 不同算法在SIPI图像数据集的实验结果
Table 18 Experimental results on the SIPI image database from different algorithms
攻击方式 PSNR 本文 [13] [14] [15] [16] 椒盐噪声 11.0086 0.8587 0.6164 0.5690 0.7542 0.7940 高斯噪声 12.2500 0.9170 0.7599 0.6611 0.7533 0.9042 中值滤波 24.8580 0.9609 0.8411 0.6904 0.9160 0.9365 维纳滤波 27.5159 0.9697 0.8878 0.7106 0.9328 0.9484 JPEG压缩 29.5265 0.9770 0.9091 0.7514 0.9456 0.9663 常规信号组合 15.6869 0.8959 0.7145 0.6211 0.7929 0.8560 偏移行列 19.8269 0.9085 0.7460 0.6755 0.8703 0.8756 偏移行列组合 17.5026 0.8222 0.6688 0.6184 0.7712 0.7743 缩放 29.0496 0.9843 0.9105 0.7622 0.9536 0.9721 旋转 13.7218 0.6798 0.5567 0.5665 0.6422 0.6416 平均值 20.0947 0.8974 0.7611 0.6626 0.8332 0.8669 表 19 不同算法在SIPI图像数据集实验结果的方差
Table 19 The variance of experimental results on the SIPI image database from different algorithms
攻击方式 本文 [13] [14] [15] [16] 椒盐噪声 0.0026 0.0030 0.0077 0.0051 0.0034 高斯噪声 0.0025 0.0055 0.0205 0.0338 0.0030 中值滤波 0.0009 0.0043 0.0242 0.0022 0.0020 维纳滤波 0.0008 0.0026 0.0260 0.0016 0.0015 JPEG压缩 0.0006 0.0011 0.0405 0.0008 0.0005 常规信号组合 0.0033 0.0034 0.0143 0.0182 0.0034 偏移行列 0.0040 0.0066 0.0180 0.0072 0.0065 偏移行列组合 0.0085 0.0053 0.0100 0.0106 0.0107 缩放 0.0002 0.0012 0.0401 0.0007 0.0004 旋转 0.0085 0.0041 0.0050 0.0080 0.0081 平均值 0.0032 0.0037 0.0206 0.0088 0.0040 表 20 不同算法构造零水印运行时间(s)
Table 20 The running time for constructing zero watermarking from different algorithms (s)
本文 [13] [14] [15] [16] Aerial 0.0343 0.5554 0.3541 6.7782 0.1607 Barbara 0.0328 0.5429 0.3494 6.7424 0.1591 Boat 0.0374 0.5429 0.3510 6.8297 0.1560 Couple 0.0328 0.5476 0.3479 6.8282 0.1560 Elain 0.0328 0.5491 0.3510 6.8079 0.1607 Frog 0.0312 0.5491 0.3416 6.7814 0.1513 Goldhill 0.0343 0.5444 0.3494 6.7814 0.1576 Zelda 0.0328 0.5600 0.3557 6.8172 0.1622 平均时间 0.0335 0.5489 0.3500 6.7958 0.1580 -
[1] 綦科, 谢冬青.基于第二代Bandelet变换的抗几何攻击图像水印.自动化学报, 2012, 38(10):1646-1653 http://www.aas.net.cn/CN/abstract/abstract17774.shtmlQi Ke, Xie Dong-Qing. Watermarking scheme against geometrical attacks based on second generation Bandelet. Acta Automatica Sinica, 2012, 38(10):1646-1653 http://www.aas.net.cn/CN/abstract/abstract17774.shtml [2] 林晓丹.基于高斯混合模型的DCT域水印检测方法.自动化学报, 2012, 38(9):1445-1448 http://www.aas.net.cn/CN/abstract/abstract17754.shtmlLin Xiao-Dan. DCT-domain watermark detection using Gaussian mixture model. Acta Automatica Sinica, 2012, 38(9):1445-1448 http://www.aas.net.cn/CN/abstract/abstract17754.shtml [3] 崔汉国, 刘健鑫, 李正民.基于金字塔技术的STL模型数字水印算法.自动化学报, 2013, 39(6):852-860 http://www.aas.net.cn/CN/abstract/abstract18111.shtmlCui Han-Guo, Liu Jian-Xin, Li Zheng-Min. STL model watermarking algorithm based on pyramid technique. Acta Automatica Sinica, 2013, 39(6):852-860 http://www.aas.net.cn/CN/abstract/abstract18111.shtml [4] 熊祥光, 韦立, 谢刚.基于3D-DCT和SVD的鲁棒彩色图像水印算法.计算机工程与科学, 2015, 37(6):1039-1100 http://or.nsfc.gov.cn/handle/00001903-5/341270Xiong Xiang-Guang, Wei Li, Xie Gang. A robust color image watermarking algorithm based on 3D-DCT and SVD. Computer Engineering and Science, 2015, 37(6):1039-1100 http://or.nsfc.gov.cn/handle/00001903-5/341270 [5] Swaminathan A, Mao Y N, Wu M. Robust and secure image hashing. IEEE Transaction on Information Forensics and Security, 2006, 1(2):215-230 doi: 10.1109/TIFS.2006.873601 [6] 牛夏牧, 焦玉华.感知哈希综述.电子学报, 2008, 36(7):1405-1411 http://kns.cnki.net/KCMS/detail/detail.aspx?filename=dzxu200807028&dbname=CJFD&dbcode=CJFQNiu Xia-Mu, Jiao Yu-Hua. An overview of perceptual hashing. Acta Electronica Sinica, 2008, 36(7):1405-1411 http://kns.cnki.net/KCMS/detail/detail.aspx?filename=dzxu200807028&dbname=CJFD&dbcode=CJFQ [7] 温泉, 孙锬锋, 王树勋.零水印的概念与应用.电子学报, 2003, 31(2):214-216 https://www.wenkuxiazai.com/doc/b60cb0f027284b73f24250b6.htmlWen Quan, Sun Tan-Feng, Wang Shu-Xun. Concept and application of zero-watermark. Acta Electronica Sinica, 2003, 31(2):214-216 https://www.wenkuxiazai.com/doc/b60cb0f027284b73f24250b6.html [8] 叶天语, 马兆丰, 钮心欣, 杨义先.强鲁棒零水印技术.北京邮电大学学报, 2010, 33(3):126-129 http://www.cqvip.com/QK/90982A/201008/34838667.htmlYe Tian-Yu, Ma Zhao-Feng, Niu Xin-Xin, Yang Yi-Xian. A zero-watermark technology with strong robustness. Journal of Beijing University of Posts and Telecommunications, 2010, 33(3):126-129 http://www.cqvip.com/QK/90982A/201008/34838667.html [9] 金炜, 励金祥, 尹曹谦.一种基于可视密码的轮廓小波图像零水印方案.光电子·激光, 2009, 20(5):653-656 https://mall.cnki.net/qikan-I-I2-JSJY-2006-01.htmlJin Wei, Li Jin-Xiang, Yin Cao-Qian. An image zero-watermarking scheme based on visual cryptography utilizing contour-wavelet. Journal of Optoelectronics·Laser, 2009, 20(5):653-656 https://mall.cnki.net/qikan-I-I2-JSJY-2006-01.html [10] 赵春晖, 刘巍.基于分块压缩感知的图像半脆弱零水印算法.自动化学报, 2012, 38(4):609-617 http://www.aas.net.cn/CN/abstract/abstract17715.shtmlZhao Chun-Hui, Liu Wei. Block compressive sensing based image semi-fragile zero-watermarking algorithm. Acta Automatica Sinica, 2012, 38(4):609-617 http://www.aas.net.cn/CN/abstract/abstract17715.shtml [11] 付剑晶, 王珂.基于第一主成分方向稳定性的图像零水印.中国图象图形学报, 2012, 17(7):756-769 doi: 10.11834/jig.20120703Fu Jian-Jing, Wang Ke. Image zero-watermark based on direction stability of first principal component vector. Journal of Image and Graphics, 2012, 17(7):756-769 doi: 10.11834/jig.20120703 [12] 周武杰, 郁梅, 禹思敏, 蒋刚毅, 葛丁飞.一种基于超混沌系统的立体图像零水印算法.物理学报, 2012, 61(8):080701 http://d.old.wanfangdata.com.cn/Periodical/wlxb201208017Zhou Wu-Jie, Yu Mei, Yu Si-Min, Jiang Gang-Yi, Ge Ding-Fei. A zero-watermarking algorithm of stereoscopic image based on hyperchaotic system. Acta Physica Sinica, 2012, 61(8):080701 http://d.old.wanfangdata.com.cn/Periodical/wlxb201208017 [13] 曲长波, 杨晓陶, 袁铎宁.小波域视觉密码零水印算法.中国图象图形学报, 2014, 19(3):365-372 doi: 10.3969/j.issn.1672-6200.2005.02.018Qu Chang-Bo, Yang Xiao-Tao, Yuan Duo-Ning. Zero-watermarking visual cryptography algorithm in the wavelet domain. Journal of Image and Graphics, 2014, 19(3):365-372 doi: 10.3969/j.issn.1672-6200.2005.02.018 [14] 叶天语.基于方差的奇异值分解域鲁棒零水印算法.光子学报, 2011, 40(6):961-966 http://www.opticsjournal.net/abstract.htm?id=OJ1106240002214A7D0FYe Tian-Yu. A robust zero-watermarking algorithm using variance in singular value decomposition domain. Acta Photonica Sinica, 2011, 40(6):961-966 http://www.opticsjournal.net/abstract.htm?id=OJ1106240002214A7D0F [15] 叶天语.抗JPEG压缩和几何攻击的鲁棒零水印算法.光子学报, 2012, 41(2):210-217 http://edu.wanfangdata.com.cn/Periodical/Detail/wxjyyy201414011Ye Tian-Yu. A robust zero-watermarking algorithm resisting JPEG compression and geometric attacks. Acta Photonica Sinica, 2012, 41(2):210-217 http://edu.wanfangdata.com.cn/Periodical/Detail/wxjyyy201414011 [16] 宋伟, 侯建军, 李赵红, 黄亮.一种基于Logistic混沌系统和奇异值分解的零水印算法.物理学报, 2009, 58(7):4449-4456 doi: 10.7498/aps.58.4449Song Wei, Hou Jian-Jun, Li Zhao-Hong, Huang Liang. A novel zero-watermarking algorithm based on Logistic chaotic system and singular value decomposition. Acta Physica Sinica, 2009, 58(7):4449-4456 doi: 10.7498/aps.58.4449 [17] Rani A, Bhullar A K, Dangwal D, Kumar S. A zero-watermarking scheme using discrete wavelet transform. Procedia Computer Science, 2015, 70:603-609 doi: 10.1016/j.procs.2015.10.046 [18] Sun L, Xu J C, Zhang X X, Dong W, Tian Y. A novel generalized Arnold transform-based zero-watermarking scheme. Applied Mathematics and Information Sciences, 2015, 9(4):2023-2035 https://www.researchgate.net/publication/307616012_Novel_zero-watermarking_scheme_based_on_DWT-DCT [19] The USC-SIPI image database[Online], available: http://sipi.usc.edu/database/, May 31, 2016 [20] UCID-uncompressed colour image database[Online], available: http://homepages.lboro.ac.uk/~cogs/datasets/UCID/ucid.html, May 31, 2016 [21] Kodak lossless true color image suite[Online], available: http://r0k.us/graphics/kodak/, May 31, 2016 -




 下载:
下载: