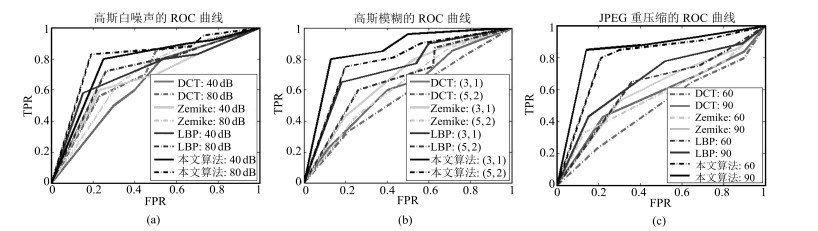
-
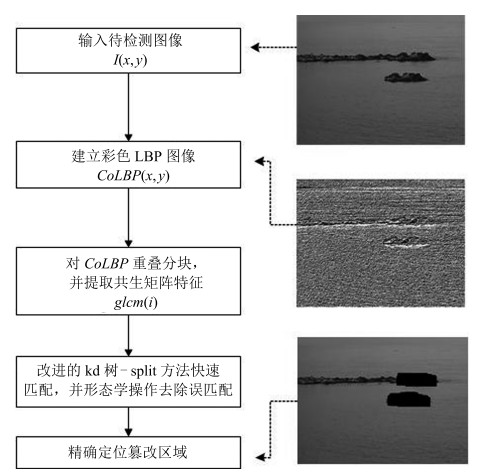
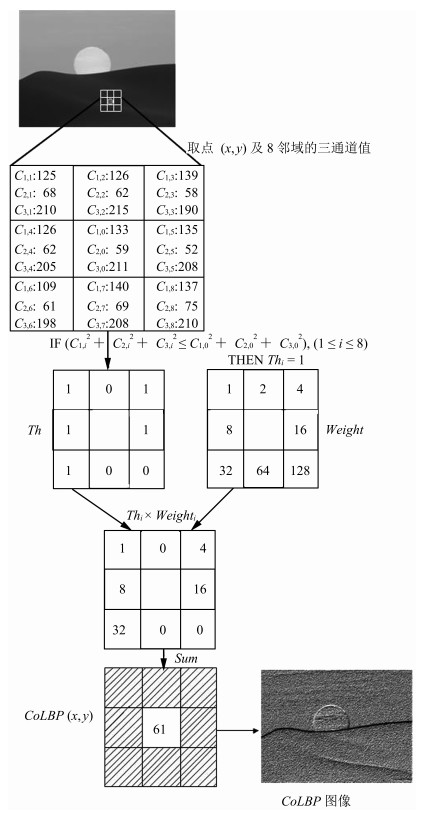
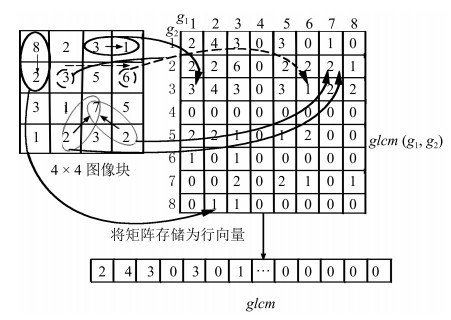
摘要: 现有的复制-粘贴盲鉴别算法大多忽略图像彩色信息,导致对隐蔽性篡改方式的检测率较低,基于此,本文提出一种基于彩色局部二值模式(Color local binary patterns,CoLBP)的隐蔽性复制-粘贴盲鉴别算法.算法首先对彩色图像进行预处理,即建立彩色LBP纹理图像,从而实现彩色信息与LBP纹理特征的融合;其次重叠分块并提取灰度共生矩阵(Gray level co-occurrence matrix,GLCM)特征;最后,提出改进的kd树和超平面划分标记split搜索方法,快速匹配图像块,并应用形态学操作去除误匹配,精确定位复制-粘贴区域.实验结果表明,本算法对隐蔽性复制-粘贴篡改定位准确,并对模糊、噪声、JPEG重压缩后处理操作有很好的鲁棒性.Abstract: Since negligence of color information in detecting copy-move forgeries leads to low accuracy in detection of in covert tampering, a novel method using color local binary patterns (CoLBP) is proposed. It involves the following three steps: first, establish color LBP texture image, which is a preprocessing of image and a combination of color information and LBP texture; second, divide into overlapping blocks and extract gray level co-occurrence matrix (GLCM) features; finally, match image blocks by the improved kd tree and split partition, remove the false matched blocks using morphological operation and then detect the resulting copy-move regions. Experimental results show that our algorithm is effective for covert tampering, and exhibits high robustness even when an image is distorted by blur, noise and JPEG recompression.1) 本文责任编委 刘成林
-
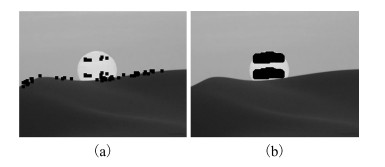
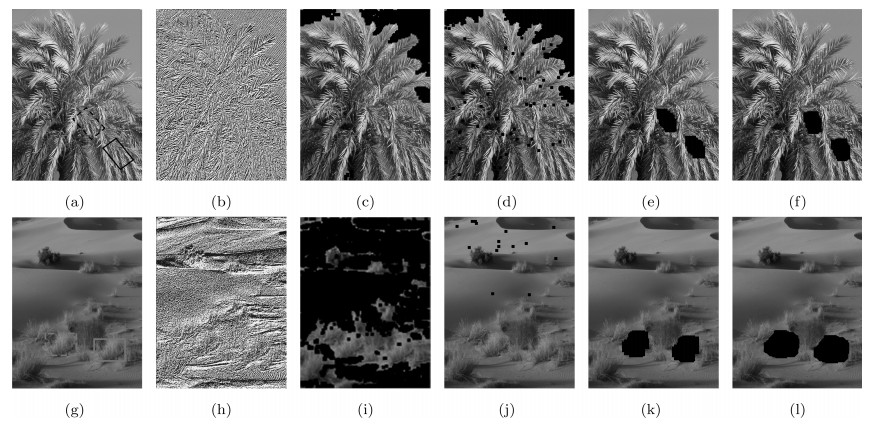
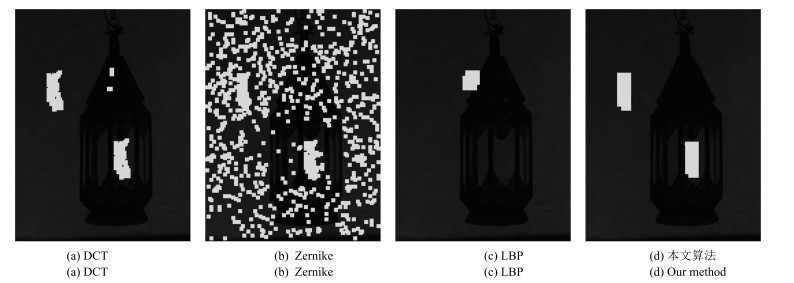
图 8 隐蔽性复制-粘贴篡改检测结果示例 ((a), (g) 隐蔽性复制-粘贴篡改图像; (b), (h) 彩色LBP图像; (c), (i) DCT[4]算法检测结果; (d), (j) Zernike[14]算法检测结果; (e), (k) LBP[17]算法检测结果; (f), (l) 本文算法检测结果.其中, (a), (g) 实线和虚线框分别表示复制和粘贴区域; (c)~(f), (i)~(l) 标记区域为算法检测篡改区域)
Fig. 8 The exemplar results on covert copy-move forgery detection ((a), (g) Covert copy-move forged images; (b), (h) Color LBP images; (c), (i) The results based on DCT[4]; (d), (j) The results based on Zernike[14]; (e), (k) The results based on LBP[17]; (f), (l) The results based on our method. Where (a), (g) solid and dashed rectangles are copied and pasted regions; (c)~(f), (i)~(l) marked regions are detected forged regions.)
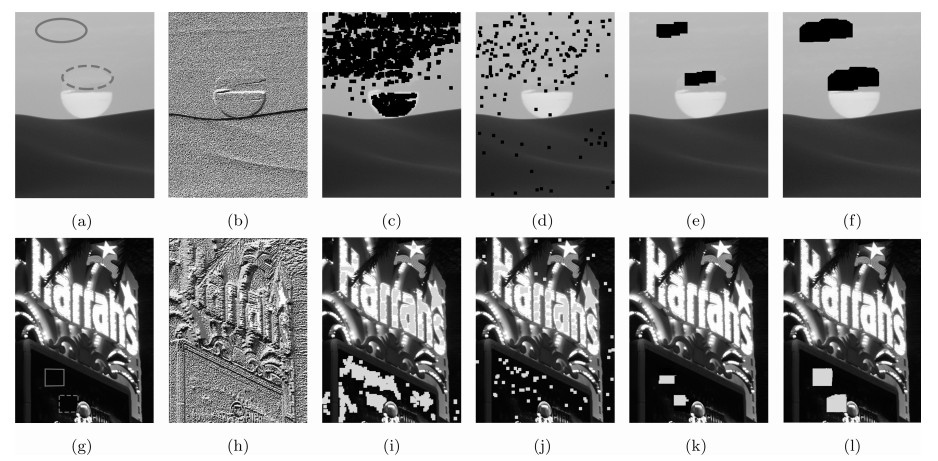
图 9 造成假象类复制-粘贴篡改检测结果示例 ((a), (g) 造成假象类复制-粘贴篡改图像; (b), (h) 彩色LBP图像; (c), (i) DCT[4]算法检测结果; (d), (j) Zernike[14]算法检测结果; (e), (k) LBP[17]算法检测结果; (f), (l) 本文算法检测结果.其中, (a), (g) 实线和虚线框分别表示复制和粘贴区域; (c)~(f), (i)~(l) 标记区域为算法检测篡改区域)
Fig. 9 The exemplar results on spurious copy-move forgery detection ((a), (g) Spurious copy-move forged images; (b), (h) Color LBP images; (c), (i) The results based on DCT[4]; (d), (j) The results based on Zernike[14]; (e), (k) The results based on LBP[17]; (f), (l) The results based on our method. Where (a), (g) solid and dashed rectangles are copied and pasted regions; (c)~(f) marked regions are detected forged regions; (i)~(l) green regions are detected forged regions.)
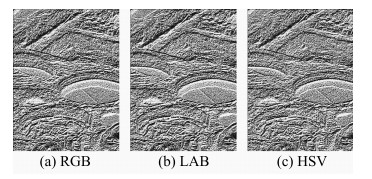
表 1 彩色空间选择分析
Table 1 The analysis on color space choice
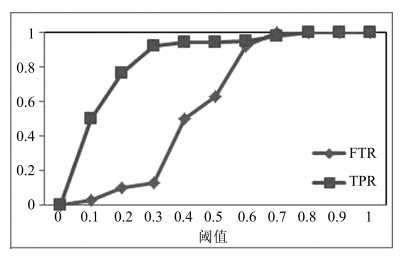
彩色空间 彩色LBP图像提取时间 (s) TPR (%) FPR (%) RGB 4 95 9 LAB 5 94 11 HSV 5.5 95 10 表 2 灰度级别gth选择
Table 2 The choice of gray level gth
灰度级别$g_{th}$ 特征维度 TPR (%) FPR (%) 4 16 85 15 8 64 91 13 16 256 95 7 32 024 95 6 -
[1] Fridrich A J, Soukal B D, Lukáš A J. Detection of copy-move forgery in digital images. In: Proceedings of the 2003 Digital Forensic Research Workshop. Cleveland, USA, 2003. [2] Wang X, Zhang X, Li Z, Wang S. A DWT-DCT based passive forensics method for copy-move attacks. In: Proceedings of the 3rd International Conference on Multimedia Information Networking and Security. Shanghai, China: IEEE, 2011. 304-308 [3] Hu J, Zhang H, Gao Q, Huang H. An improved lexicographical sort algorithm of copy-move forgery detection. In: Proceedings of the 2nd International Conference on Networking and Distributed Computing. Beijing, China: IEEE, 2011. 23-27 [4] Cao Y J, Gao T G, Li F, Yang Q T. A robust detection algorithm for copy-move forgery in digital images. Forensic Science International, 2012, 214(1-3): 33-43 doi: 10.1016/j.forsciint.2011.07.015 [5] Popescu A C, Farid H. Exposing Digital Forgeries by Detecting Duplicated Image Regions, Technical Report 2004-515, Dartmouth College, USA, 2004. [6] 骆伟祺, 黄继武, 丘国平.鲁棒的区域复制图像篡改检测技术.计算机学报, 2007, 30(11): 1998-2007 http://www.cnki.com.cn/Article/CJFDTOTAL-JSJX200711013.htmLuo Wei-Qi, Huang Ji-Wu, Qiu Guo-Ping. Robust detection of region-duplication forgery in digital image. Chinese Journal of Computers, 2007, 30(11): 1998-2007 http://www.cnki.com.cn/Article/CJFDTOTAL-JSJX200711013.htm [7] Muhammad G, Hussain M, Bebis G. Passive copy move image forgery detection using undecimated dyadic wavelet transform. Digital Investigation, 2012, 9(1): 49-57 doi: 10.1016/j.diin.2012.04.004 [8] Bayram S, Sencar H T, Memon N. An efficient and robust method for detecting copy-move forgery. In: Proceedings of the 2009 IEEE International Conference on Acoustics, Speech and Signal Processing. Taipei, China: IEEE, 2009. 1053-1056 [9] Zhong J L, Gan Y F. Detection of copy-move forgery using discrete analytical Fourier-Mellin transform. Nonlinear Dynamics, 2016, 84(1): 189-202 doi: 10.1007/s11071-015-2374-9 [10] Zhang T, Wang R. Copy-move forgery detection based on SVD in digital image. In: Proceedings of the 2nd International Congress on Image and Signal Processing. Tianjin, China: IEEE, 2009. 1-5 [11] Liu G J, Wang J W, Lian S G, Wang Z Q. A passive image authentication scheme for detecting region-duplication forgery with rotation. Journal of Network and Computer Applications, 2011, 34(5): 1557-1565 doi: 10.1016/j.jnca.2010.09.001 [12] Mahdian B, Saic S. Detection of copy-move forgery using a method based on blur moment invariants. Forensic Science International, 2007, 171(2-3): 180-189 doi: 10.1016/j.forsciint.2006.11.002 [13] Ryu S J, Lee M J, Lee H K. Detection of copy-rotate-move forgery using Zernike moments. In: Proceedings of the 12th International Conference on Information Hiding. Calgary, AB, Canada: Springer, 2010. 51-65 [14] Ryu S J, Kirchner M, Lee M J, Lee H K. Rotation invariant localization of duplicated image regions based on Zernike moments. IEEE Transactions on Information Forensics and Security, 2013, 8(8): 1355-1370 doi: 10.1109/TIFS.2013.2272377 [15] Li L D, Li S S, Zhu H C, Wu X Y. Detecting copy-move forgery under affine transforms for image forensics. Computers and Electrical Engineering, 2014, 40(6): 1951-1962 doi: 10.1016/j.compeleceng.2013.11.034 [16] Lynch G, Shih F Y, Liao H Y M. An efficient expanding block algorithm for image copy-move forgery detection. Information Sciences, 2013, 239: 253-265 doi: 10.1016/j.ins.2013.03.028 [17] Davarzani R, Yaghmaie K, Mozaffari S, Tapak M. Copy-move forgery detection using multiresolution local binary patterns. Forensic Science International, 2013, 231(1-3): 61-72 doi: 10.1016/j.forsciint.2013.04.023 [18] Cozzolino D, Poggi G, Verdoliva L. Efficient dense-field copy-move forgery detection. IEEE Transactions on Information Forensics and Security, 2015, 10(11): 2284-2297 doi: 10.1109/TIFS.2015.2455334 [19] Porebski A, Vandenbroucke N, Macaire L. Haralick feature extraction from LBP images for color texture classification. In: Proceedings of the 1st Workshops on Image Processing Theory, Tools and Applications. Sousse: IEEE, 2008. 1-8 [20] Haralick R M. Statistical and structural approaches to texture. Proceedings of the IEEE, 1979, 67(5): 786-804 doi: 10.1109/PROC.1979.11328 [21] Amerini I, Ballan L, Caldelli R, Del Bimbo A, Serra G. A SIFT-based forensic method for copy-move attack detection and transformation recovery. IEEE Transactions on Information Forensics and Security, 2011, 6(3): 1099-1110 doi: 10.1109/TIFS.2011.2129512 [22] Kakar P, Sudha N. Exposing post processed copy-paste forgeries through transform-invariant features. IEEE Transactions on Information Forensics and Security, 2012, 7(3): 1018-1028 doi: 10.1109/TIFS.2012.2188390 -




 下载:
下载: