A Robust Byzantine Fault-tolerant Consensus Algorithm Against Adaptive Attack Based on Ring Signature and Threshold Signature
-
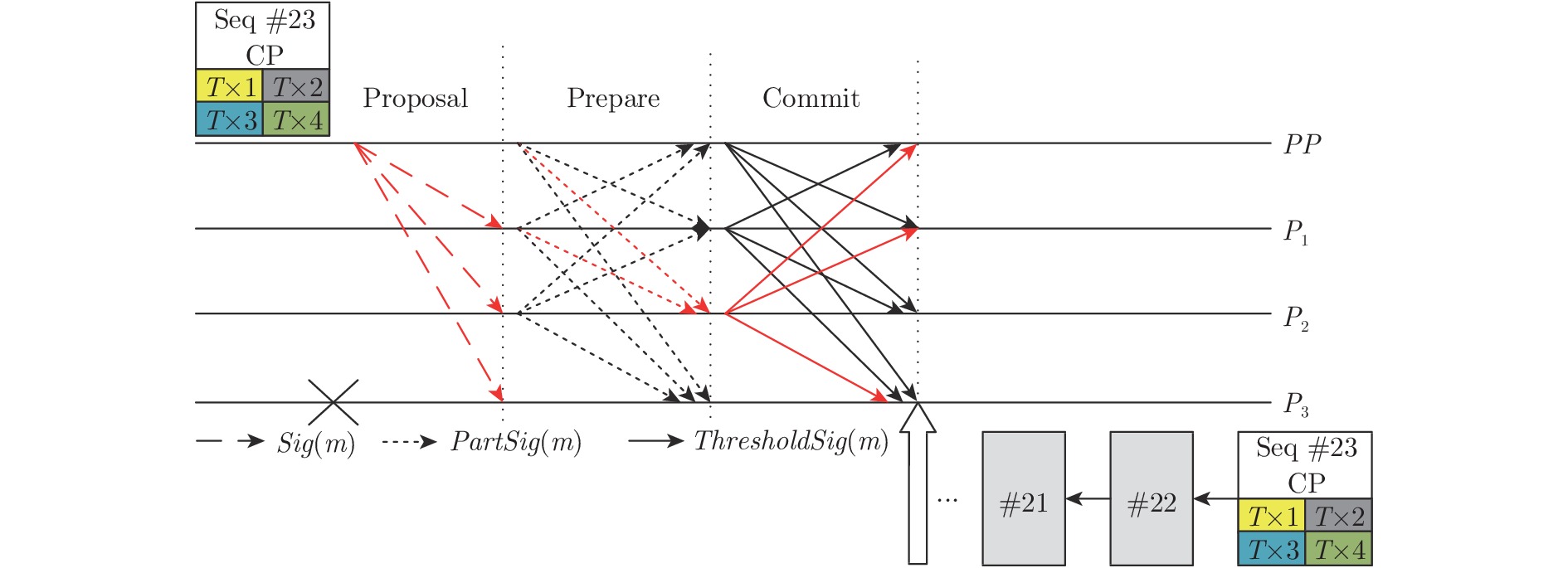
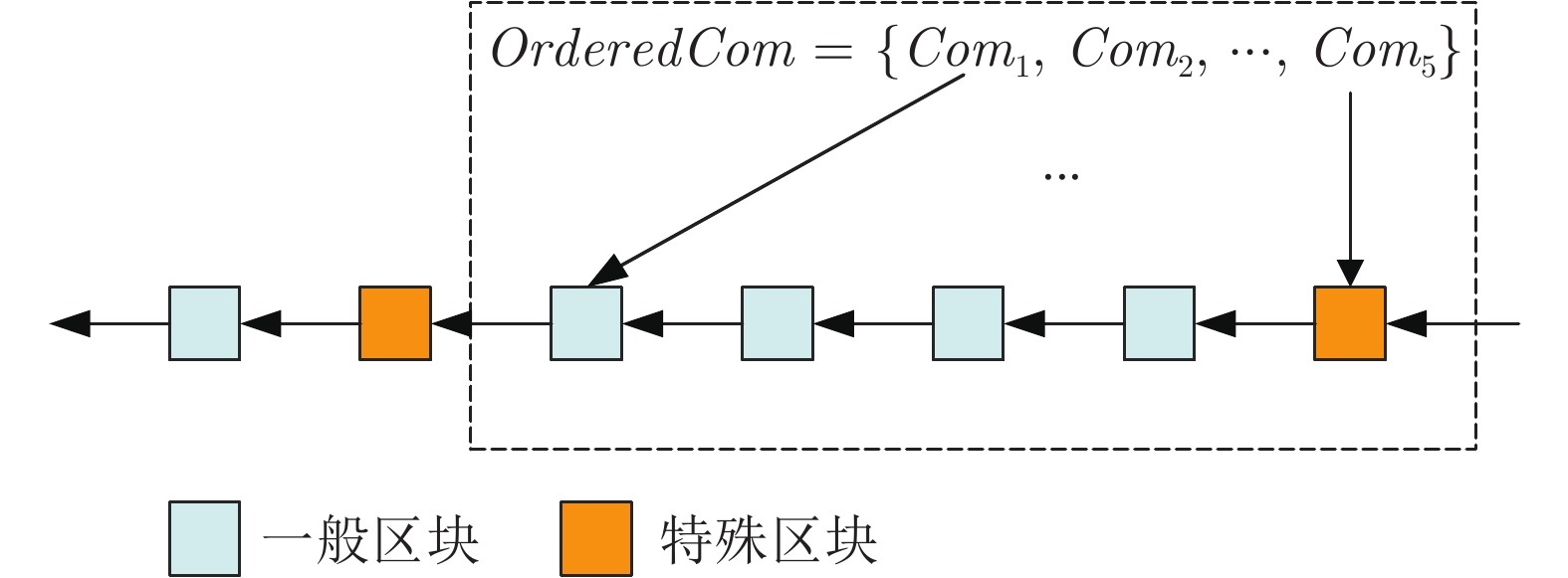
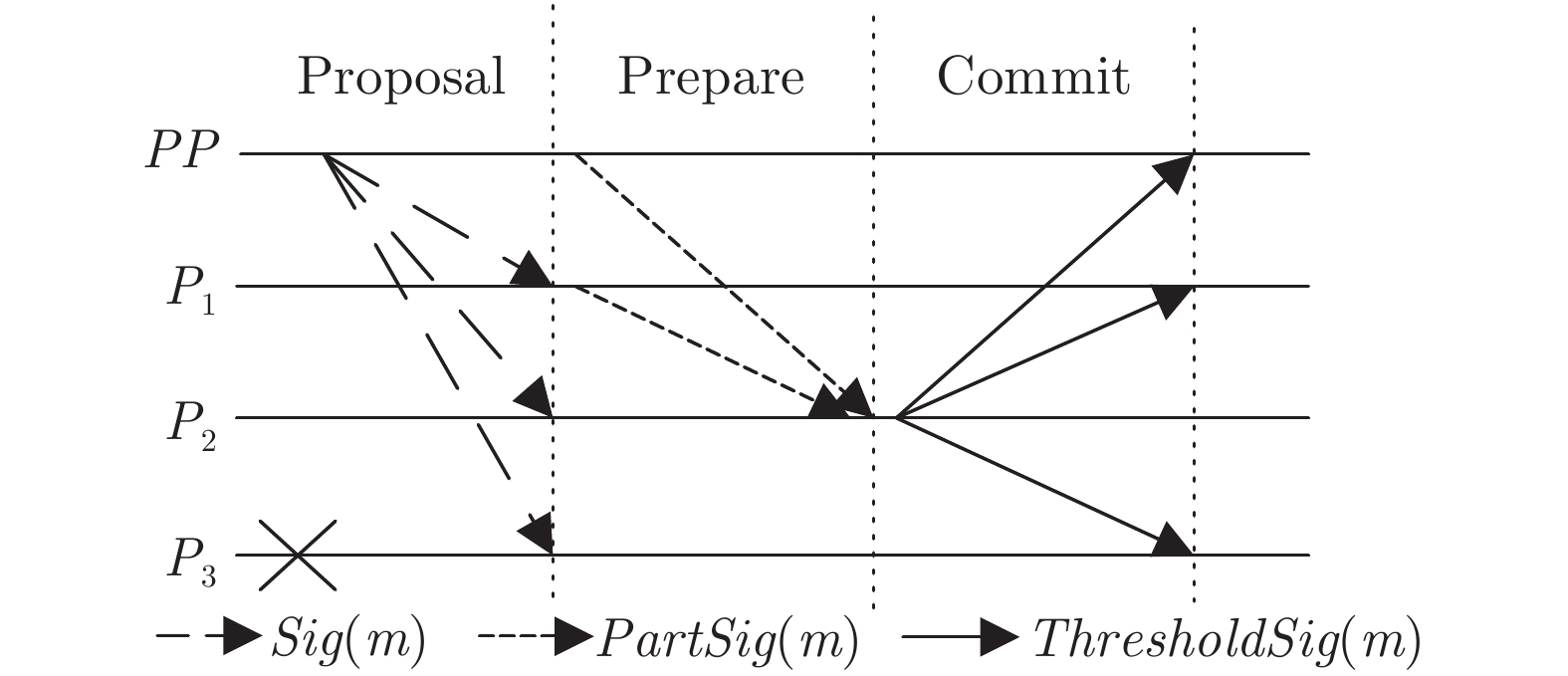
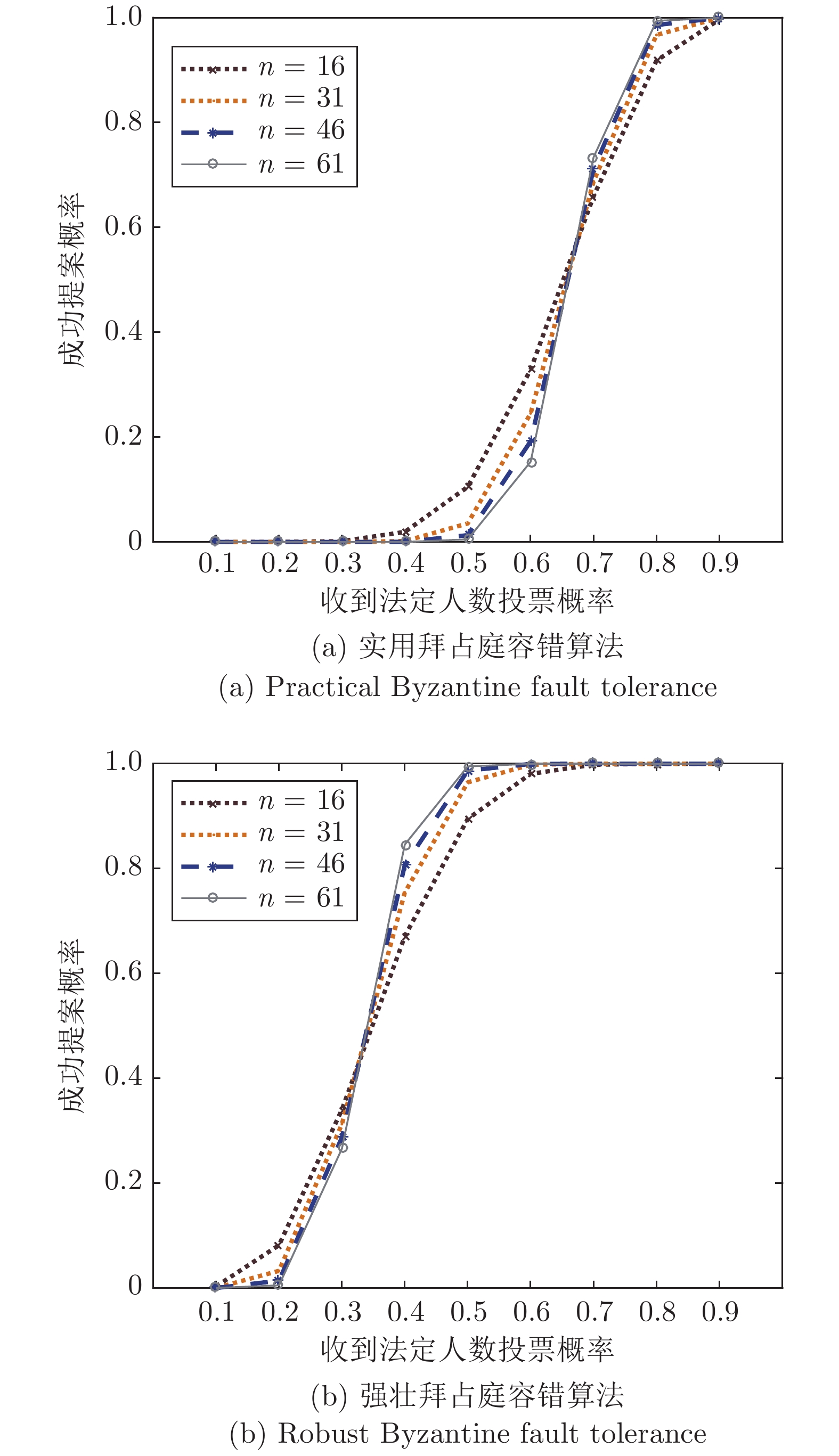
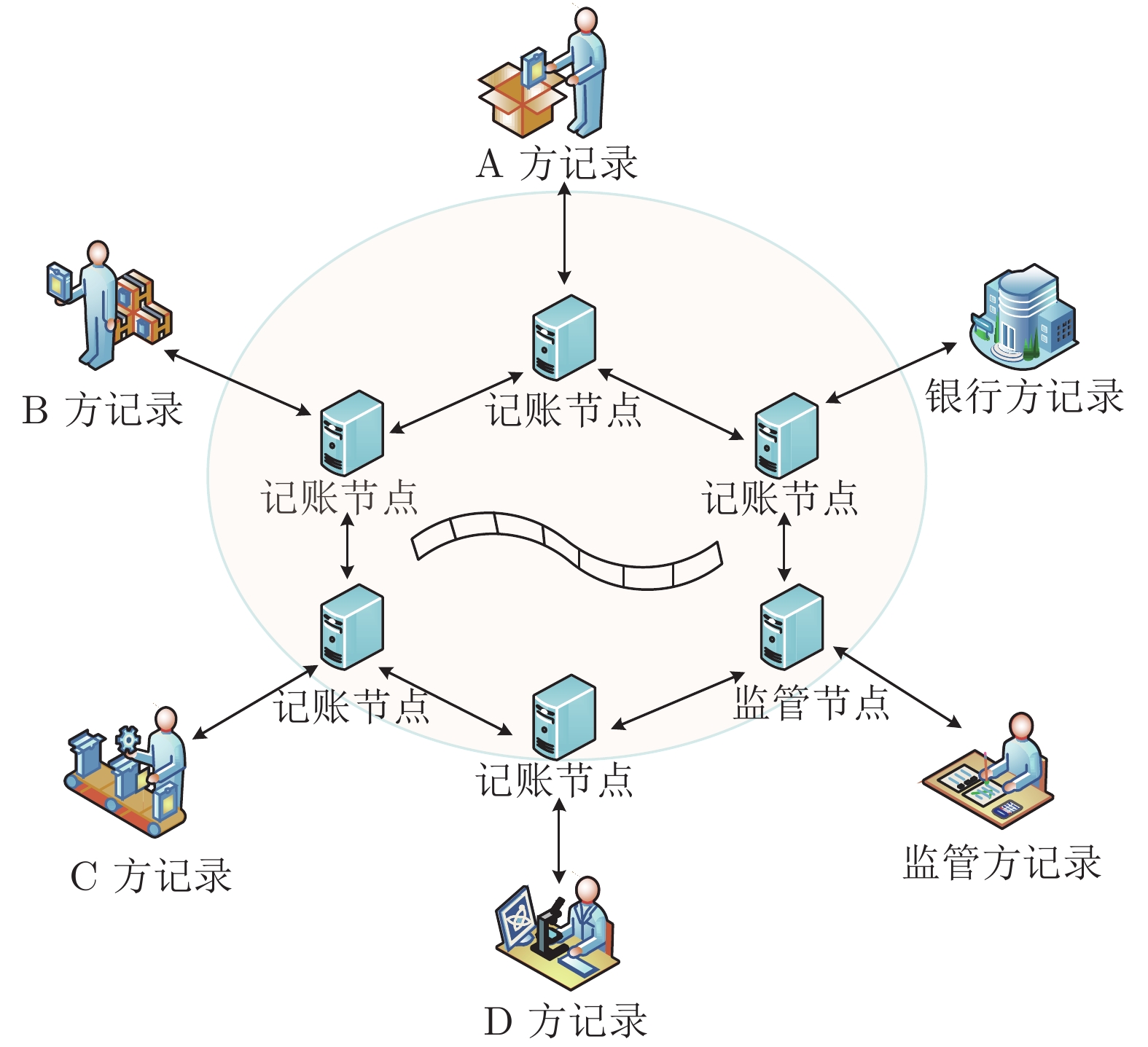
摘要: 共识算法作为区块链底层关键技术, 可解决决策权分散的分布式系统中的一致性难题. 良好的共识算法可提升系统健壮性, 但大多数方案在网络故障或主动攻击下存在鲁棒性不可控、活性表现差、可扩展性不足等问题. 针对上述问题, 提出一种抗自适应攻击的健壮拜占庭容错共识算法(Robust Byzantine fault tolerance, RBFT). 该算法利用环签名的无条件强匿名性构造排序选主算法, 隐匿选举每一轮共识中的提案者, 进而达到模糊敌手攻击对象、有效抵抗自适应攻击的目的. 同时, 通过在多轮投票中合成代表法定人数投票意愿的门限签名, 将网络划分为众多最小连通性网络, 以保证在最小连通性网络环境中实现低延迟、高鲁棒性的拜占庭容错共识算法. 分析表明, 系统在提升可扩展性、减少视图更换、降低签名验证开销的同时, 能够有效保证系统活性.Abstract: As the fundamental key technology of blockchain, consensus algorithms can resolve the consistency problem in the distributed system with decentralized decision-making authority. Fine-designed consensus algorithms can improve the robustness of system, but most of the schemes have the drawbacks of uncontrollable robustness, poor activity performance and insufficient scalability in the case of network failure or active attack scenarios. Given problems above, this paper proposes a robust Byzantine fault tolerance (RBFT) algorithm resistant to adaptive attacks. Using the ring signature with unconditional strong anonymity, the RBFT algorithm constructs an ordering and master-selecting algorithm to anonymously elect the proposer of every round of consensus, by which the attack object can be obscured from the adaptive attack. Meanwhile, by generating the threshold signature of the designated voters, the network is divided into a number of minimum connected networks to ensure consensus with low latency and high robustness. The analysis shows that by using the proposed RBFT algorithm, the system scalability can be improved, view change frequency and signature verification overhead can be reduced, at the same time the system activity can be effectively guaranteed.
-
Key words:
- Blockchain /
- Byzantine fault tolerance /
- consensus algorithm /
- adaptive attack /
- ring signature /
- threshold signature
-
表 1 拜占庭容错算法性能对比
Table 1 The performance comparison of Byzantine fault tolerant algorithm
表 2 链码接口
Table 2 Chain code interface
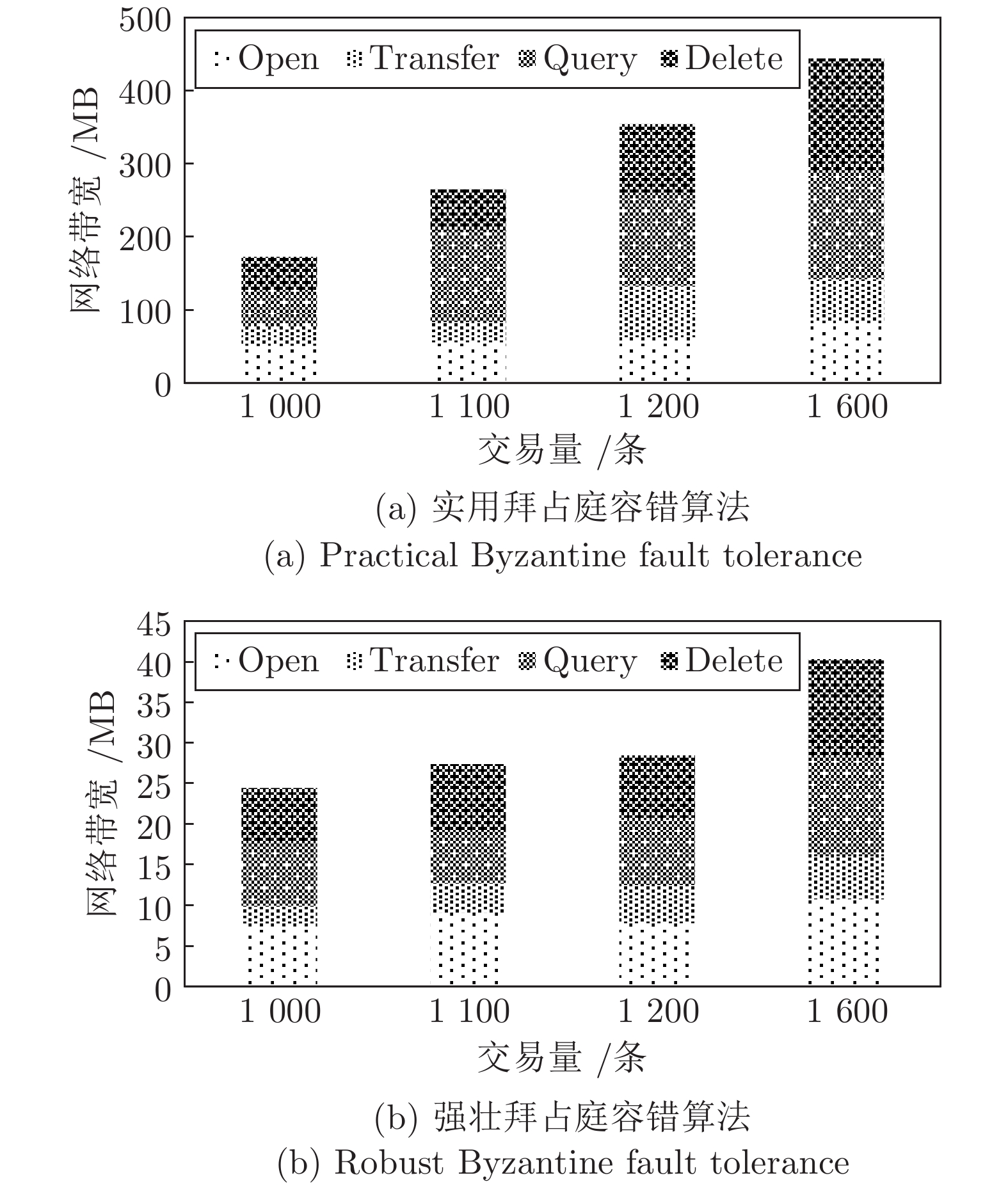
接口名 接口功能 接口接收参数 Open 开户 账户名、金额 Query 查询 账户名 Invoke 转账 账户名、账户名、金额 Delete 销户 账户名 -
[1] 袁勇, 王飞跃. 区块链技术发展现状与展望. 自动化学报, 2016, 42(4): 481-494 doi: 10.16383/j.aas.2016.c160158Yuan Yong, Wang Fei-Yue. Blockchain: The state of the art and future trends. Acta Automatica Sinica, 2016, 42(4): 481-494 doi: 10.16383/j.aas.2016.c160158 [2] Nakamoto S. Bitcoin: A peer-to-peer electronic cash system [Online], available: https://pdos.csail.mit.edu/6.824/papers/bitcoin.pdf, October 31, 2008 [3] 袁勇, 倪晓春, 曾帅, 王飞跃. 区块链共识算法的发展现状与展望. 自动化学报, 2018, 44(11): 2011-2022 doi: 10.16383/j.aas.2018.c180268Yuan Yong, Ni Xiao-Chun, Zeng Shuai, Wang Fei-Yue. Blockchain consensus algorithms: The state of the art and future trends. Acta Automatica Sinica, 2018, 44(11): 2011-2022 doi: 10.16383/j.aas.2018.c180268 [4] Gervais A, Karame G O, Wüst K, Glykantzis V, Ritzdorf H, Capkun S. On the security and performance of proof of work blockchains. In: Proceedings of the ACM SIGSAC Conference on Computer and Communications Security. Vienna, Austria: ACM, 2016. 3−16 [5] Vasin P. Blackcoin's proof-of-stake protocol v2 [Online], available: https://blackcoin.org/blackcoin-pos-protocol-v2-whitepaper.pdf, September 1, 2014 [6] Larimer D. Delegated proof-of-stake (DPOS) [Online], available: https://bitcointalk.org/index.php?topic=558316.0, April 3, 2014 [7] Lamport L, Shostak R, Pease M. The Byzantine generals problem. ACM Transactions on Programming Languages and Systems, 1982, 4(3): 382-401 doi: 10.1145/357172.357176 [8] Castro M, Liskov B. Practical byzantine fault tolerance. In: Proceedings of the 3rd Symposium on Operating Systems Design and Implementation. New Orleans, USA: USENIX Association, 1999. 173−186 [9] Kotla R, Alvisi L, Dahlin M, Clement A, Wong E. Zyzzyva: Speculative byzantine fault tolerance. ACM SIGOPS Operating Systems Review, 2007, 41(6): 45-58 doi: 10.1145/1323293.1294267 [10] Xu H, Long Y, Liu Z Q, Liu Z, Gu D W. Dynamic practical Byzantine fault tolerance. In: Proceedings of the IEEE Conference on Communications and Network Security (CNS). Beijing, China: IEEE, 2018. 1−8 [11] Correia M, Neves N F, Verissimo P. How to tolerate half less one byzantine nodes in practical distributed systems. In: Proceedings of the 23rd IEEE International Symposium on Reliable Distributed Systems. Florianopolis, Brazil: IEEE, 2004. 174−183 [12] Veronese G S, Correia M, Bessani A N, Lung L C, Verissimo P. Efficient byzantine fault-tolerance. IEEE Transactions on Computers, 2013, 62(1): 16-30 doi: 10.1109/TC.2011.221 [13] Cowling J A, Myers D S, Liskov B, Rodrigues R, Shrira L. HQ replication: A hybrid quorum protocol for Byzantine fault tolerance. In: Proceedings of the 7th Symposium on Operating Systems Design and Implementation. Seattle, USA: USENIX Association, 2006. 177−190 [14] Gueta G G, Abraham I, Grossman S, Malkhi D, Pinkas B, Reiter M, et al. SBFT: A scalable and decentralized trust infrastructure. In: Proceedings of the 49th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). Portland, USA: IEEE, 2019. 568−580 [15] Yin M F, Malkhi D, Reiter M K, Gueta G G, Abraham I. HotStuff: BFT consensus with linearity and responsiveness. In: Proceedings of the ACM Symposium on Principles of Distributed Computing. Toronto, Canada: ACM, 2019. 347−356 [16] Kwon J. Tendermint: Consensus without mining [Online], available: http://diyhpl.us/~bryan/papers2/bitcoin/tendermint_v03.pdf, November 8, 2014 [17] Pass R, Shi E. Hybrid consensus: Efficient consensus in the permissionless model. In: Proceedings of the 31st International Symposium on Distributed Computing. Vienna, Austria: Schloss Dagstuhl-Leibniz-Zentrum für Informatik, 2017. 1−16 [18] Kokoris-Kogias E, Jovanovic P, Gailly N, Khoffi I, Gasser L, Ford B. Enhancing bitcoin security and performance with strong consistency via collective signing. In: Proceedings of the 25th USENIX Security Symposium. Washington, USA: USENIX Association, 2016. 279−296 [19] Pass R, Shi E. Thunderella: Blockchains with optimistic instant confirmation. In: Proceedings of the 37th Annual International Conference on the Theory and Applications of Cryptographic Techniques. Tel Aviv, Israel: Springer, 2018. 3−33 [20] Li P L, Wang G S, Chen X Q, Xu W. Gosig: Scalable byzantine consensus on adversarial wide area network for blockchains. arXiv preprint arXiv: 1802.01315, 2018. [21] Gilad Y, Hemo R, Micali S, Vlachos G, Zeldovich N. Algorand: Scaling byzantine agreements for cryptocurrencies. In: Proceedings of the 26th Symposium on Operating Systems Principles. Shanghai, China: ACM, 2017. 51−68 [22] Rivest R L, Shamir A, Tauman Y. How to leak a secret. In: Proceedings of the 7th International Conference on the Theory and Application of Cryptology and Information Security. Gold Coast, Australia: Springer, 2001. 552−565 [23] Liu J K, Wei V K, Wong D S. Linkable spontaneous anonymous group signature for ad hoc groups. In: Proceedings of the 9th Australasian Conference on Information Security and Privacy. Sydney, Australia: Springer, 2004. 325−335 [24] Park C, Kurosawa K. New EIGamal type threshold digital signature scheme. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, 1996, 79-A(1): 86-93 -




 下载:
下载: