|
[1]
|
Zhang X M, Han Q L, Ge X H, Ding D R, Ding L, Yue D, Peng C. Networked control systems: a survey of trends and techniques. IEEE/CAA Journal of Automatica Sinica. 2020, 7(1): 1-17 doi: 10.1109/JAS.2019.1911861
|
|
[2]
|
Sun Q, Lim C C, Shi P, Liu F. Design and stability of moving horizon estimator for Markov jump linear systems. IEEE Transactions on Automatic Control. 2019, 64(3): 1109-1124 doi: 10.1109/TAC.2018.2816102
|
|
[3]
|
Mousavinejad E, Yang F, Han Q L, Vlacic L. A novel cyber attack detection method in networked control systems. IEEE Transactions on Cybernetics. 2018, 48(11): 3254-3264 doi: 10.1109/TCYB.2018.2843358
|
|
[4]
|
Dolk V S, Tesi P, De Persis C, Heemels W P M H. Event-triggered control systems under denial-of-service attacks. IEEE Transactions on Control of Network Systems. 2017, 4(1): 93-105 doi: 10.1109/TCNS.2016.2613445
|
|
[5]
|
Langner R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Security & Privacy. 2011, 9(3): 49-51
|
|
[6]
|
Cherdantseva Y, Burnap P, Blyth A, Eden P, Jones K, Soulsby H, Stoddart K. A review of cyber security risk assessment methods for SCADA systems. Computers & Security. 2016, 56: 1-27
|
|
[7]
|
王琦, 邰伟, 汤奕, 倪明. 面向电力信息物理系统的虚假数据注入攻击研究综述. 自动化学报. 2019, 45(1): 72-83Wang Qi, Tai Wei, Tang Yi, Ni Ming. A review on false data injection attack toward cyber-physical power system. ACTA AUTOMATICA SINICA. 2019, 45(1): 72-83
|
|
[8]
|
Kurmanaev A, Herrera I. No end in sight to Venezuelas Blackout, experts warn [Online], available: https://www.nytimes.com/2019/03/11/world/americas/venzuela-blackout-maduro.html, July 15, 2019
|
|
[9]
|
刘烃, 田决, 王稼舟, 吴宏宇, 孙利民, 周亚东, 沈超, 管晓宏. 信息物理融合系统综合安全威胁与防御研究. 自动化学报. 2019, 45(1): 5-24Liu Ting, Tian Jue, Wang Jia-Zhou, Wu Hong-Yu, Sun Li-Min, Zhou Ya-Dong, Shen Chao, Guan Xiao-Hong. Integrated security threats and defense of cyber-physical systems. ACTA AUTOMATICA SINICA. 2019, 45(1): 5-24
|
|
[10]
|
Dibaji S M, Pirani M, Flamholz D, Annaswamy A M, Johansson K H, Chakrabortty A. A systems and control perspective of CPS security. Annual Reviews in Control. 2019, 47: 394-411 doi: 10.1016/j.arcontrol.2019.04.011
|
|
[11]
|
Murguia C, Van De Wouw N, Ruths J. Reachable sets of hidden CPS sensor attacks: Analysis and synthesis tools. IFAC-PapersOnLine. 2017, 50(1): 2088-2094 doi: 10.1016/j.ifacol.2017.08.528
|
|
[12]
|
Macwan R, Drew C, Panumpabi P, Valdes A, Vaidya N, Sauer P, et al. Collaborative defense against data injection attack in IEC61850 based smart substations. In: Proceedings of the IEEE Power and Energy Society General Meeting. Boston, MA, USA: IEEE, 2016. 1−5
|
|
[13]
|
An L W, Yang G H. Secure state estimation against sparse sensor attacks with adaptive switching mechanism. IEEE Transactions on Automatic Control. 2018, 63(8): 2596-2603 doi: 10.1109/TAC.2017.2766759
|
|
[14]
|
Zhou Y, Vamvoudakis K G, Haddad W M, Jiang Z P. A secure control learning framework for cyber-physical systems under sensor and actuator attacks. IEEE Transactions on Cybernetics, 2021, 51(9): 4648-4660
|
|
[15]
|
李雪, 李雯婷, 杜大军, 孙庆, 费敏锐. 拒绝服务攻击下基于UKF的智能电网动态状态估计研究. 自动化学报. 2019, 45(1): 120-131Li Xue, Li Wen-Ting, Du Da-Jun, Sun Qing, Fei Min-Rui. Dynamic state estimation of smart grid based on UKF under denial of service attacks. ACTA AUTOMATICA SINICA. 2019, 45(1): 120-131
|
|
[16]
|
Ma L F, Wang Z D, Han Q L, Lam H K. Variance-constrained distributed filtering for time-varying systems with multiplicative noises and deception attacks over sensor networks. IEEE Sensors journal. 2017, 17(7): 2279-2288 doi: 10.1109/JSEN.2017.2654325
|
|
[17]
|
Su L, Ye D. A cooperative detection and compensation mechanism against Denial-of-Service attack for cyber-physical systems. Information Sciences. 2018, 444: 122-134 doi: 10.1016/j.ins.2018.02.066
|
|
[18]
|
Zhao C H, Mallada E, Dirfler F. Distributed frequency control for stability and economic dispatch in power networks. In: Proceedings of the American Control Conference. Chicago, IL, USA: IEEE, 2015. 2359−2364
|
|
[19]
|
Shitharth S, Prince W D. An enhanced optimization based algorithm for intrusion detection in SCADA network. Computers & Security. 2017, 70: 16-26
|
|
[20]
|
Guo Z Y, Shi D W, Johansson K H, Shi L. Optimal linear cyberattack on remote state estimation. IEEE Transactions on Control of Network Systems. 2017, 4(1): 4-13 doi: 10.1109/TCNS.2016.2570003
|
|
[21]
|
Mo Y L, Sinopoli B. On the performance degradation of cyber-physical systems under stealthy integrity attacks. IEEE Transactions on Automatic Control. 2016, 61(9): 2618-2624 doi: 10.1109/TAC.2015.2498708
|
|
[22]
|
Chen Y, Kar, S, Moura J M F. Cyber-Physical attacks with control objectives. IEEE Transactions on Automatic Control. 2018, 63(5): 1418-1425 doi: 10.1109/TAC.2017.2741778
|
|
[23]
|
Mo Y L, Sinopoli B. Secure control against replay attacks. In: Proceedings of the 47th Annual Allerton Conference on Communication, Control, and Computing, Allerton 2009. Monticello, USA: IEEE, 2009. 911−918
|
|
[24]
|
Rubio Hernan J, De Cicco L, Garcia Alfaro J. On the use of watermark-based schemes to detect cyber-physical attacks. Eurasip Journal on Information Security, 2017: Article No. 8
|
|
[25]
|
Fang C G, Qi Y F, Cheng P, Zheng W X. Optimal periodic watermarking schedule for replay attack detection in cyber-physical systems. Automatica. 2020, 112: 108698 doi: 10.1016/j.automatica.2019.108698
|
|
[26]
|
Teixeira A M, Ferrari R M. Detection of sensor data injection attacks with multiplicative watermarking. In: Proceedings of 2018 European Control Conference. Limassol, Cyprus: IEEE, 2018. 338−343
|
|
[27]
|
Song Z, Skuric A, Ji K. A recursive watermark method for hard real-time industrial control system cyber-resilience Enhancement. IEEE Transactions on Automation Science and Engineering. 2020, 17(2): 1030-1043 doi: 10.1109/TASE.2019.2963257
|
|
[28]
|
Satchidanandan B, Kumar P R. Dynamic watermarking: Active defense of networked cyber-physical systems. Proceedings of the IEEE. 2017, 105(2): 219-240 doi: 10.1109/JPROC.2016.2575064
|
|
[29]
|
Satchidanandan B, Kumar P R. On the design of securityguaranteeing dynamic watermarks. IEEE Control Systems Letters. 2020, 4(2): 307-312 doi: 10.1109/LCSYS.2019.2925278
|
|
[30]
|
Huang T, Satchidanandan B, Kumar P R, Xie L. An online detection framework for cyber-attacks on automatic generation control. IEEE Transactions on Power Systems. 2018, 33(6): 6816–6827 doi: 10.1109/TPWRS.2018.2829743
|
|
[31]
|
Zhao D, Ding S X, Karimi H R, Li Y Y. Robust H∞ filtering for two-dimensional uncertain linear discrete time-varying systems: A Krein space-based method. IEEE Transactions on Automatic Control. 2019, 64(12): 5124-5131 doi: 10.1109/TAC.2019.2908699
|
|
[32]
|
Lai T L, Wei C Z. Least squares estimates in stochastic regression models with applications to identification and control of dynamic systems. Annals of Statistics. 1982, 10(1): 154-166 doi: 10.1214/aos/1176345697
|
|
[33]
|
Hu X M, Zou Q, Zou H B. Design and application of fractional order predictive functional control for industrial heating furnace. IEEE Access. 2018, 6: 66565-66575 doi: 10.1109/ACCESS.2018.2878554
|
|
[34]
|
Naghnaeian M, Hirzallah N H, Voulgaris P G. Security via multirate control in cyber-physical systems. Systems & Control Letters. 2019, 124: 12-18
|



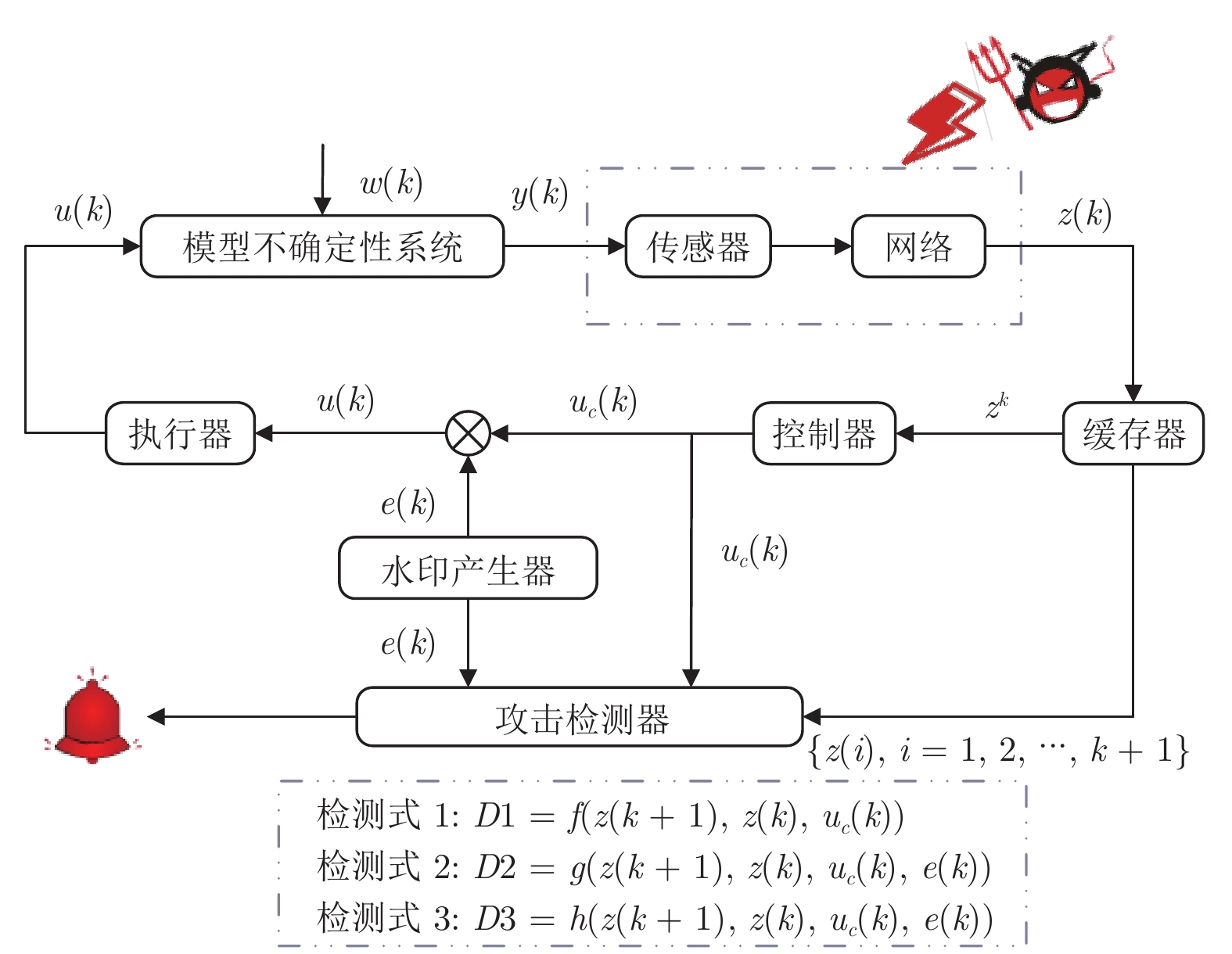
 下载:
下载: