-
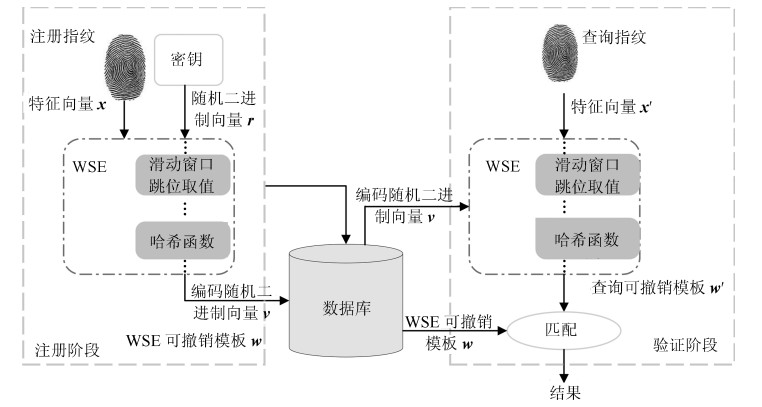
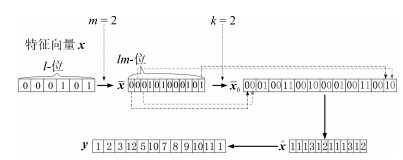
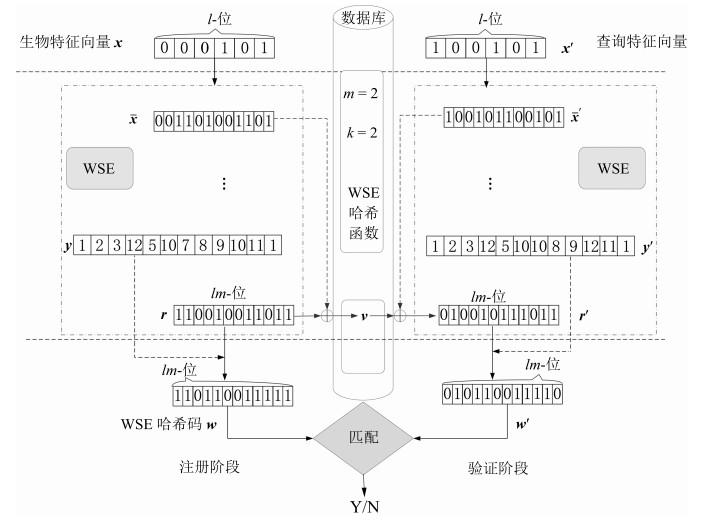
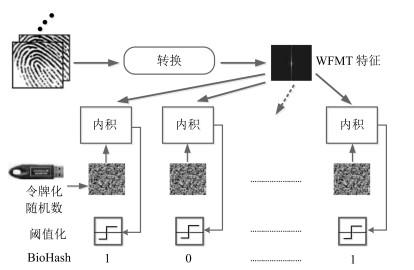
摘要: 将令牌化随机数作为外部因子的双因子可撤销生物特征认证方法存在令牌泄露、丢失等安全威胁. 本文提出了一种生物特征作为唯一输入的解决方法, 即单因子的可撤销生物特征认证方法. 首先, 利用扩展的特征向量, 通过预定义的滑动窗口和哈希函数随机化生成二进制种子; 然后替换不同的辅助数据来生成可撤销模板; 最后, 由查询生物特征向量对辅助数据进行解码, 提高了性能和安全性. 在指纹数据库FVC2002和FVC2004的实验结果表明, 该方法不仅满足可撤销生物特征识别的4个设计标准, 同时防御了3种安全攻击.Abstract: Two-factor cncellable biometrics use tokenized random number as an external factor, however, tokenized factor incurs severe security and privacy threats. In this paper, we propose a one-factor cancellable biometrics scheme, which requires sole biometric as input. First, it exploits an expanded feature vector, generating seeds of randomized binary auxiliary data by sliding a pre-defined window and Hash function, which enhances performance and security. Then, the cancellable template hence can be generated by replacing different binary auxiliary data. Finally, the auxiliary data is decoded by using sole query biometric. The experiments have been conducted on FVC2002 and FVC2004 databases, and results show that the scheme does not only fulfill four design criteria of cancellable biometrics but also resist to the threat model that enclosed three security attacks.
-
Key words:
- Biometrics /
- template protection /
- cancellable /
- one-factor /
- two-factor
1) 本文责任编委 黄庆明 -
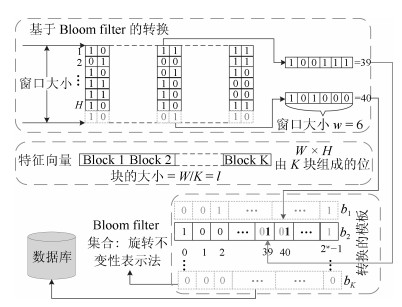
表 1 各种生物特征模板保护算法的比较结果
Table 1 Comparative result of various biometric template protection methods
可撤销方案 转换方式 相似性 缺点 Biohashing[5] 随机投影+二值化处理 汉明距离 原始模板可由折衷密钥推算出来 Wang等[12] 离散傅里叶变换+随机投影 汉明距离 性能下降 Bloom filter[13] Bloom filter (十进制到二进制映射) 汉明距离 易受暴力攻击 P-MCC[17] KL投影+二值化 汉明距离 可撤销性弱 2P-MCC[18] 完全/部分置换 汉明距离 用户需要管理密钥 GRP-based IoM Hashing[10] 多重随机投影+记录最大值索引 欧氏距离 性能下降 URP-based IoM Hashing[10] 置换+记录最大值索引 欧氏距离 性能下降 BioEncoding[19] 布尔函数 汉明距离 易受ARM攻击 表 2 WSE哈希处理效率(s) (${m}=1 000$, ${k}=3$)
Table 2 Processing efficiency of WSE Hashing (s) (${m}=1 000$, $k=3$)
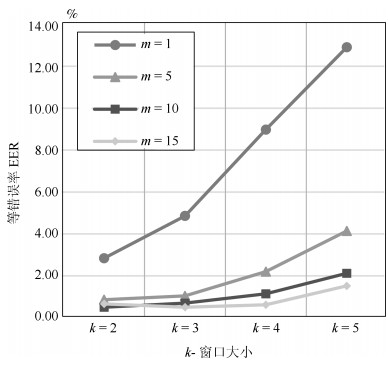
平均时间 FVC2002-DB1 FVC2002-DB2 FVC2004-DB1 FVC2004-DB2 注册阶段 0.035031 0.034884 0.034481 0.033151 验证阶段 0.034896 0.034874 0.034621 0.034647 表 3 不同方法的性能精度对比(EER) (%)
Table 3 EER comparison between proposed method and other methods (%)
方法 FVC2002-DB1 FVC2002-DB2 FVC2004-DB1 FVC2004-DB2 WSE Hashing 0.2 0.62 2.6 7.13 Binary fingerprint vector (Baseline)[11] 0.26 0.12 1.58 4.39 URP-based IoM Hashing[10] 0.46 2.1 4.51 8.02 GRP-based IoM Hashing[10] 0.22 0.47 4.74 4.1 Bloom filter[24] 2.3 1.8 13.4 8.1 2P-MCC$_{64, 64}$[18] 3.3 1.8 6.3 _ EFV Hashing[7] 0.32 0.63 2.62 7.14 表 4 不可链接性的全局度量($D_{\underset\longleftrightarrow{{\rm sys}}}$) (${m}=1 000$, ${k}=3$)
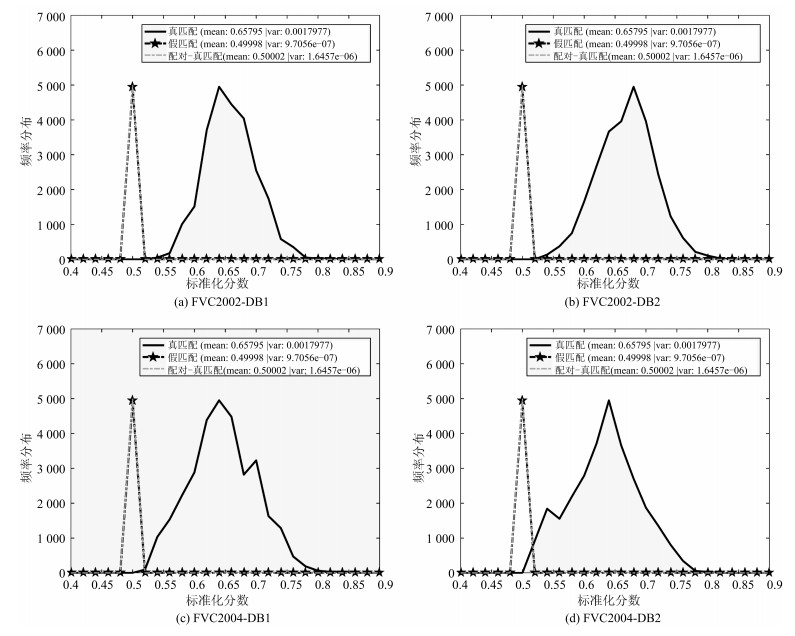
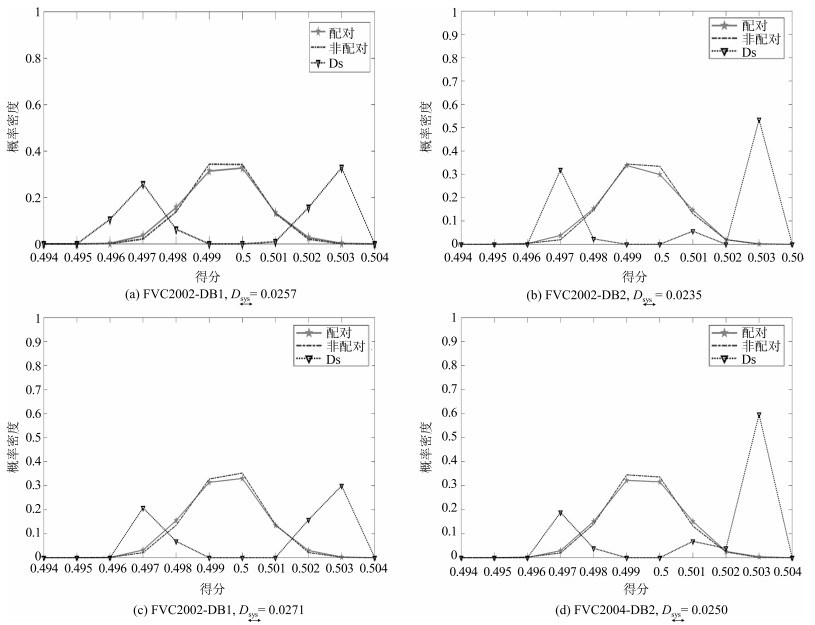
Table 4 Global measure ($D_{\underset\longleftrightarrow{{\rm sys}}}$) of unlinkability (${m}=1 000$, ${k}=3$)
方法 FVC2002-DB1 FVC2002-DB2 FVC2004-DB1 FVC2004-DB2 WSE Hashing 0.0257 0.0235 0.0271 0.0250 EFV Hashing[7] 0.0404 0.0473 0.0465 0.0459 -
[1] 张宁, 臧亚丽, 田捷. 生物特征与密码技术的融合-一种新的安全身份认证方案. 密码学报, 2015, 2(2): 159-176 https://www.cnki.com.cn/Article/CJFDTOTAL-MMXB201502006.htmZhang Ning, Zang Ya-Li, Tian Jie. The integration of biometrics and cryptography-a new solution for secure identity authentication. Journal of Cryptologic Research, 2015, 2(2): 159-176 https://www.cnki.com.cn/Article/CJFDTOTAL-MMXB201502006.htm [2] 许秋旺, 张雪锋. 基于细节点邻域信息的可撤销指纹模板生成算法. 自动化学报, 2017, 43(4): 645-652 doi: 10.16383/j.aas.2017.c160069Xu Qiu-Wang, Zhang Xue-Feng. Generating cancelable flngerprint templates using minutiae local information. Acta Automatica Sinica, 2017, 43(4): 645-652 doi: 10.16383/j.aas.2017.c160069 [3] 王慧珊, 张雪锋. 基于Biohashing的指纹模板保护算法. 自动化学报, 2018, 44(4): 760-768 doi: 10.16383/j.aas.2017.c170056Wang Hui-Shan, Zhang Xue-Feng. Improved biohashing fingerprint template protection algorithms. Acta Automatica Sinica, 2018, 44(4): 760-768 doi: 10.16383/j.aas.2017.c170056 [4] 梁耀, 冯冬芹, 徐珊珊, 陈思媛, 高梦州. 加密传输在工控系统安全中的可行性研究. 自动化学报, 2018, 44(3): 434-442 doi: 10.16383/j.aas.2018.c160399Liang Yao, Feng Dong-Qin, Xu Shan-Shan, Chen Si-Yuan, Gao Meng-Zhou. Feasibility analysis of encrypted transmission on security of industrial control systems. Acta Automatica Sinica, 2018, 44(3): 434-442 doi: 10.16383/j.aas.2018.c160399 [5] Jin A T B, Ling D N C, Goh A. Biohashing: two factor authentication featuring fingerprint data and tokenised random number. Pattern Recognition, 2004, 37(11): 2245-2255 doi: 10.1016/j.patcog.2004.04.011 [6] Patel V M, Ratha N K, Chellappa R. Cancelable biometrics: A review. IEEE Signal Processing Magazine, 2015, 32(5): 54-65 doi: 10.1109/MSP.2015.2434151 [7] Lee M J, Jin Z, Teoh A B J. One-factor cancellable scheme for fingerprint template protection: extended feature vector (EFV) Hashing. In: Proceedings of the 2018 IEEE International Workshop on Information Forensics and Security. New York, USA: IEEE, 2018. 1-7 [8] Jin Z, Lim M H, Teoh A B J, Goi B M, Tay Y H. Generating fixed-length representation from minutiae using kernel methods for fingerprint authentication. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 2016, 46(10): 1415-1428 doi: 10.1109/TSMC.2015.2499725 [9] Wang S, Deng G, Hu J K. A partial Hadamard transform approach to the design of cancelable fingerprint templates containing binary biometric representations. Pattern Recognition, 2017, 61: 447-458 doi: 10.1016/j.patcog.2016.08.017 [10] Jin Z, Hwang J Y, Lai Y L, Kim S, Teoh A B J. Ranking-based locality sensitive hashing-enabled cancelable biometrics: Index-of-max hashing. IEEE Transactions on Information Forensics and Security, 2018, 13(2): 393-407 doi: 10.1109/TIFS.2017.2753172 [11] Cheung K H, Kong A W K, You J, Zhang D. An analysis on accuracy of cancelable biometrics based on biohashing. In: Proceedings of the 2005 International Conference on Imaging Science, Systems, and Technology. Berlin, Germany: Springer-Verlag, 2005. 40-45 [12] Wang S, Hu J K. Alignment-free cancelable fingerprint template design: A densely infinite-to-one mapping (DITOM) approach. Pattern Recognition, 2012, 45(12): 4129-4137 doi: 10.1016/j.patcog.2012.05.004 [13] Rathgeb C, Breitinger F, Busch C, Baier H. On application of bloom filters to iris biometrics. IET Biometrics, 2014, 3(4): 207-218 doi: 10.1049/iet-bmt.2013.0049 [14] Hermans J, Mennink B, You J, Peeters R. When a bloom filter is a doom filter: Security assessment of a novel iris biometric te mplate protection system. In: Proceedings of the 2014 Biometrics Special Interest Group. New York, USA: IEEE, 2014. 1-6 [15] Bringer J, Morel C, Rathgeb C. Security analysis of bloom filter-based iris biometric template protection. In: Proceedings of the 2015 International Conference on Biometrics. New York, USA: IEEE, 2015. 527-534 [16] Cappelli R, Ferrara M, Maltoni D. Minutia cylinder-code: A new representation and matching technique for fingerprint recognition. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2010, 32(12): 21-28 http://ieeexplore.ieee.org/document/5432197 [17] Ferrara M, Maltoni D, Busch C, Cappelli R. Noninvertible minutia cylinder-code representation. IEEE Transactions on Information Forensics and Security, 2012, 7(6): 1727-1737 doi: 10.1109/TIFS.2012.2215326 [18] Ferrara M, Maltoni D, Cappelli R. A two-factor protection scheme for MCC fingerprint templates. In: Proceedings of the 2014 Biometrics Special Interest Group. New York, USA: IEEE, 2014. 1-8 [19] Ouda O, Tsumura N, Nakaguchi T. Tokenless cancelable biometrics scheme for protecting iriscodes. In: Proceedings of the 2010 International Conference on Pattern Recognition. New York, USA: IEEE, 2010. 882-885 [20] Kang J, Nyang D H, Lee K H. Two-factor face authentication using matrix permutation transformation and a user password. Information Sciences, 2014, 269(8): 1-20 [21] Maio D, Maltoni D, Cappelli R, Wayman J, Jain A K. FVC2002: Second fingerprint verification competition. In: Proceedings of the 16th International Conference on Pattern Recognition. New York, USA: IEEE, 2002. 811-814 [22] Maio D, Maltoni D, Cappelli R, Wayman J, Jain A K. FVC2004: Third fingerprint verification competition. Biometric Authentication. Berlin: Springer-Verlag, 2004. 1-7 [23] Cappelli R, Maio D, Maltoni D, Wayman J L, Jain A K. Performance evaluation of fingerprint verification systems. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2006, 28(1): 3-18 doi: 10.1109/TPAMI.2006.20 [24] Li G Q, Yang B, Rathgeb C, Busch C. Towards generating protected fingerprint templates based on bloom filters. In: Proceedings of the 2015 International Workshop on Biometrics and Forensics. New York, USA: IEEE, 2015. 1-6 [25] Gomez-Barrero M, Galbally J, Rathgeb C. General framework to evaluate unlinkability in biometric template protection systems. IEEE Transactions on Information Forensics and Security, 2018, 13(6): 1406-1420 doi: 10.1109/TIFS.2017.2788000 [26] Tams B, Mihailescu P, Munk A. Security considerations in minutiae-based fuzzy vaults. IEEE Transactions on Information Forensics and Security, 2017, 10(5): 985-998 http://smartsearch.nstl.gov.cn/paper_detail.html?id=5786ed8a1699649291bcd06d0610383d -



 下载:
下载: