A 2D Structure Entropy-based Approach to Security Assessment of Communication-based Train Control System
-
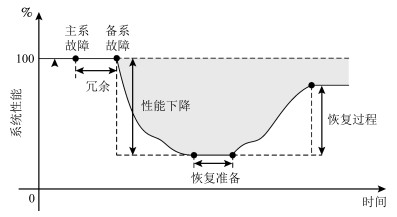
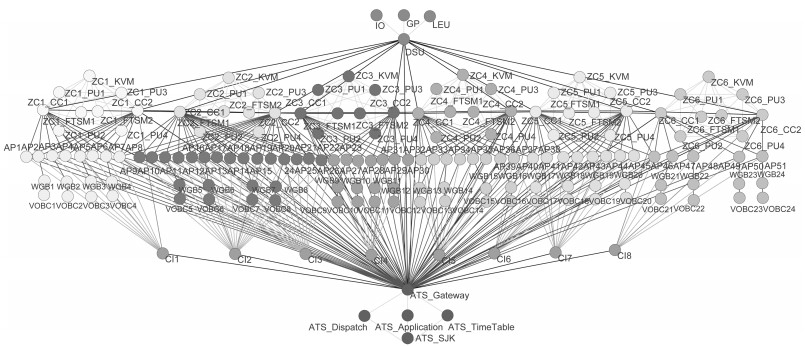
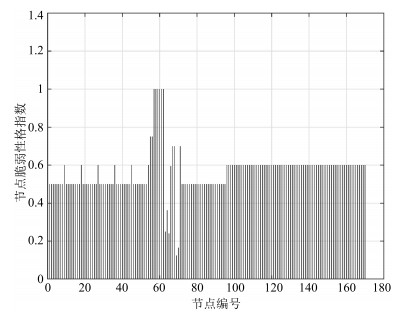
摘要: 随着计算机技术、通信技术和控制技术在城市轨道交通列车运行控制系统中的应用,城市轨道交通的自动化和信息化程度不断提升.然而,基于通信的列车运行控制(Communication-based train control,CBTC)技术采用的通用计算机设备和通信技术带来的信息安全漏洞,给CBTC系统带来了日益严峻的信息安全风险,因此,对CBTC系统的信息安全风险进行量化、动态评估具有重要意义.本文根据设备及通信链路的差异性构建了CBTC网络拓扑模型,结合信息安全风险下线路列车运行性能变化导致的运能损失,采用综合表征信息域和物理域特征的二维结构信息熵对CBTC系统信息安全风险进行建模分析.最后,基于城市轨道交通列控系统半实物仿真平台对评估方法进行验证,表明所提方法对CBTC系统信息安全量化评估的有效性和准确性.
-
关键词:
- 基于通信的列车运行控制 /
- 信息安全风险评估 /
- 结构信息熵 /
- 列车运行性能 /
- 半实物仿真平台
Abstract: With the wide application of computer, communication and control technologies in train operation control system, the degree of automation and informatization of urban rail transit is continuously improved. However, universal computer equipment and communication technologies adopted by the method of CBTC (communication-based train control) bring serious security risks to the CBTC system. In view of this, it is of great significance to quantify and dynamically evaluate the information security risks of CBTC system. In this paper, a topology model of CBTC networks is built according to the characteristics of equipment and communication links. Combining the capacity loss from performance changes of train control under security risks, the 2D structural information entropy is constructed, which can comprehensively characterize the cyber space and physical space features, to model and evaluate the information security risks of CBTC system. Finally, with a hardware-in-the-loop simulation platform for urban rail transit CBTC security, the effectiveness and accuracy of the proposed approach are verified.1) 本文责任编委 吕宜生 -
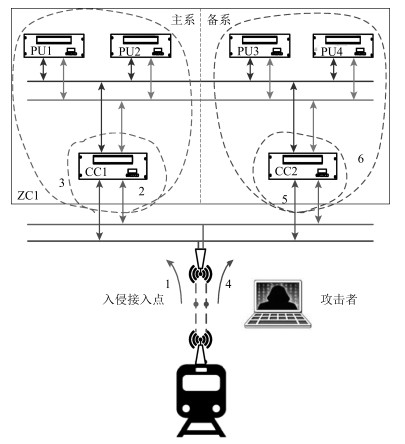
表 1 通信链路的安全性
Table 1 Security of communication links between equipments
通信方式 通信协议 数据安全性 被截获的难易程度 综合评价 边权重 RSSP-I 2 3 2.3 3 有线 私有协议 3 3 3 1 明文 1 4 1.9 5 无线 RSSP-I 2 2 2 4 私有协议 3 1 2.4 2 -
[1] 张霄, 丁智, 吴云双, 谢宗星.城市轨道交通发展现状及前景浅析.现代城市, 2014, 9(2):17-19 http://d.old.wanfangdata.com.cn/Conference/9277207Zhang Xiao, Ding Zhi, Wu Yun-Shuang, Xie Zong-Xing. Analysis on present situation and prospects of city rail traffic development. Modern City, 2014, 9(2):17-19 http://d.old.wanfangdata.com.cn/Conference/9277207 [2] 郑莹.基于无线通信的CBTC研究综述.通信技术, 2011, 44(12):137-138, 141 doi: 10.3969/j.issn.1002-0802.2011.12.046Zheng Ying. Study on CBTC based on wireless communication. Communications Technology, 2011, 44(12):137-138, 141 doi: 10.3969/j.issn.1002-0802.2011.12.046 [3] 洪翔.轨道交通自动化信息安全面临的挑战与应对(节选).自动化博览, 2015, (2):26 http://d.old.wanfangdata.com.cn/Periodical/zdhbl2015020011Hong Xiang. Challenges and countermeasures for information security of rail transportation automation (excerpt). Automation Panorama, 2015, (2):26 http://d.old.wanfangdata.com.cn/Periodical/zdhbl2015020011 [4] 陈登科.城市轨道交通信号系统网络安全分析.铁路通信信号工程技术, 2012, 9(5):41-43 doi: 10.3969/j.issn.1673-4440.2012.05.013Chen Deng-Ke. Network safety analysis of urban rail transit signaling system. Railway Signalling and Communication Engineering, 2012, 9(5):41-43 doi: 10.3969/j.issn.1673-4440.2012.05.013 [5] Bloomfield R, Bendele M, Bishop P, Stroud R, Tonks S. The risk assessment of ERTMS-based railway systems from a cyber security perspective: methodology and lessons learned. In: Proceedings of the 1st International Conference on Reliability, Safety, and Security of Railway Systems. Modelling, Analysis, Verification, and Certification. Paris, France: Springer, 2016. 3-19 [6] 邝香琦. CBTC系统信息安全风险评估方法研究[硕士学位论文], 北京交通大学, 中国, 2017.Kuang Xiang-Qi. Research on Risk Assessment Method of Information Security in Communication-Based Train Control Systems[Master thesis], Beijing Jiaotong University, China, 2017. [7] Craven P V, Craven S. Security of ATCS wireless railway communications. In: Proceedings of the 2005 ASME/IEEE Joint Rail Conference. Pueblo, CO, USA: IEEE, 2005. 227238 [8] 郁舒雅.城市轨道交通列控系统信息安全检测技术研究[硕士学位论文], 北京交通大学, 中国, 2017.Yu Shu-Ya. Research on Information Security Detection Technology of Urban Rail Transit Control System[Master thesis], Beijing Jiaotong University, China, 2017. [9] 包正堂.列控系统信息安全风险主动防御研究[硕士学位论文], 北京交通大学, 中国, 2017.Bao Zheng-Tang. Active Defense of Security Risk in Train Control System[Master thesis], Beijing Jiaotong University, China, 2017. [10] Chen B B, Schmittner C, Ma Z D, Temple W G, Dong X S, Jones D L, et al. Security analysis of urban railway systems: the need for a cyber-physical perspective. In: Proceedings of the 2015 SAFECOMP Workshops on Computer Safety, Reliability, and Security. Delft, The Netherlands: Springer, 2014. 277-290 [11] 李文武, 游文霞, 王先培.电力系统信息安全研究综述.电力系统保护与控制, 2011, 39(10):140-147 http://d.old.wanfangdata.com.cn/Periodical/jdq201110026Li Wen-Wu, You Wen-Xia, Wang Xian-Pei. Survey of cyber security research in power system. Power System Protection and Control, 2011, 39(10):140-147 http://d.old.wanfangdata.com.cn/Periodical/jdq201110026 [12] 詹全忠, 陈岚.浅谈水利网络与信息安全体系.水利信息化, 2010, (5):31-33 doi: 10.3969/j.issn.1674-9405.2010.05.007Zhan Quan-Zhong, Chen Lan. A brief discuss on water resources network and information security system. Water Resources Informatization, 2010, (5):31-33 doi: 10.3969/j.issn.1674-9405.2010.05.007 [13] 胡江, 孙国臣, 张加军, 侯秦脉.由"震网"病毒事件浅议核电站信息安全现状及监管.核科学与工程, 2015, 35(1):181-185 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=hkxygc201501028Hu Jiang, Sun Guo-Chen, Zhang Jia-Jun, Hou Qin-Mai. The status quo and information security supervision of NPP from stuxnet attacks. Chinese Journal of Nuclear Science and Engineering, 2015, 35(1):181-185 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=hkxygc201501028 [14] Mendes E. Introduction to Bayesian networks. Practitioner's Knowledge Representation. Berlin, Heidelberg: Springer, 2014. 67-71 [15] Xie P, Li J H, Ou X M, Liu P, Levy R. Using Bayesian networks for cyber security analysis. In: Proceedings of the 2010 IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). Chicago, IL, USA: IEEE, 2010. 211-220 [16] Shin J, Son H, Ur R K, Heo G. Development of a cyber security risk model using bayesian networks. Reliability Engineering and System Safety, 2015, 134:208-217 doi: 10.1016/j.ress.2014.10.006 [17] Shin J, Son H, Heo G. Cyber security risk evaluation of a nuclear I & C using BN and ET. Nuclear Engineering and Technology, 2016, 49(3):517-524 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=17463e3b6050eaf5123530c8648a82cc [18] Schneier B. Attack trees. Doctor Dobbs Journal, 1999, 24(12):21-29 http://d.old.wanfangdata.com.cn/Periodical/zwxb200712012 [19] Mauw S, Oostdijk M. Foundations of attack trees. Information Security and Cryptology-ICISC 2005. Berlin, Heidelberg: Springer, 2006. 186-198 [20] Ten C W, Liu C C, Govindarasu M. Vulnerability assessment of cybersecurity for SCADA systems using attack trees. In: Proceedings of the 2007 IEEE Power Engineering Society General Meeting. Tampa, FL, USA: IEEE, 2007. 18 [21] Murata T. Petri nets:properties, analysis and applications. Proceedings of the IEEE, 1989, 77(4):541-580 doi: 10.1109/5.24143 [22] Chen T M, Sanchez-Aarnoutse J C, Buford J. Petri net modeling of cyber-physical attacks on smart grid. IEEE Transactions on Smart Grid, 2011, 2(4):741-749 doi: 10.1109/TSG.2011.2160000 [23] El Bouchti A, Haqiq A. Modeling cyber-attack for SCADA systems using CoPNet approach. In: Proceedings of the 2012 IEEE International Conference on Complex Systems (ICCS). San Agadir, Morocco: IEEE, 2012. 1-6 [24] Jensen K, Rozenberg G. High-Level Petri Nets: Theory and Application. Berlin, New York: Springer, 1991. [25] Zhou S J, Qin Z G, Zhang F, Zhang X F, Chen W, Liu J D. Colored petri net based attack modeling. In: Proceedings of the 9th International Conference on Rough Sets, Fuzzy Sets, Data Mining, and Granular Computing. Chongqing, China: Springer, 2003. 715-718 [26] Roy S, Ellis C, Shiva S, Dasgupta D, Shandilya V, Wu Q S. A survey of game theory as applied to network security. In: Proceedings of the 43rd Hawaii International Conference on System Sciences. Honolulu, HI, USA: IEEE, 2010. 1-10 [27] Liang X N, Xiao Y. Game theory for network security. IEEE Communications Surveys and Tutorials, 2013, 15(1):472486 http://d.old.wanfangdata.com.cn/OAPaper/oai_arXiv.org_1307.3136 [28] Cui X L, Tan X B, Zhang Y, Xi H S. A Markov game theory-based risk assessment model for network information system. In: Proceedings of the 2008 International Conference on Computer Science and Software Engineering. Wuhan, China: IEEE, 2008. 1057-1061 [29] Li A S, Pan Y C. Structural information and dynamical complexity of networks. IEEE Transactions on Information Theory, 2016, 62(6):3290-3339 doi: 10.1109/TIT.2016.2555904 [30] Li A S, Hu Q F, Liu J, Pan Y C. Resistance and security index of networks: structural information perspective of network security. Scientific Reports, 2016, 6: Article No.26810 [31] Shannon C E. A mathematical theory of communication. Bell System Technical Journal, 1948, 27(3):379-423 doi: 10.1002/bltj.1948.27.issue-3 [32] Anand K, Bianconi G. Entropy measures for networks: toward an information theory of complex topologies. Physical Review E: Covering Statistical, Nonlinear, and Soft Matter Physics, 2009, 80(4): Article No.045102 [33] Dong H Y, Wang H W, Tang T. An attack tree-based approach for vulnerability assessment of communication-based train control systems. In: Proceedings of the 2017 Chinese Automation Congress (CAC). Ji'nan, China: IEEE, 2017. 6407-6412 -




 下载:
下载: