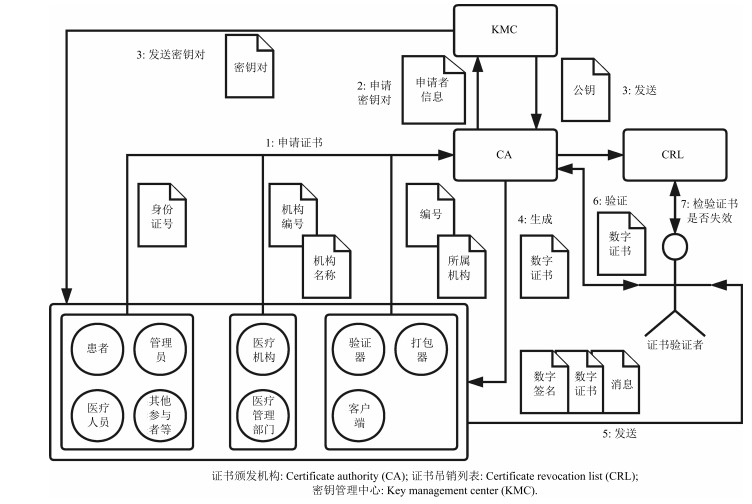
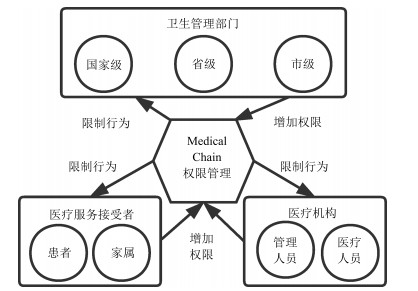
-
摘要: 医疗数据共享、防篡改、防泄漏一直是困扰医疗行业的难题.一位患者在转诊时,往往无法提供以往的就诊信息,原因在于国内各医院医疗信息大多数情况下无法共享,而仅能通过病历、检验单等极易丢失的纸质信息来实现一部分医疗信息的共享.同时,患者的医疗信息极易造成泄露,在出现医疗纠纷时所提供的医疗信息也无法保证真实性与公正性.本文设计了一个基于实用拜占庭容错算法(Practical Byzantine fault tolerance,PBFT)的联盟式医疗区块链系统,该系统是一个多节点共同维护与共享的,并且能够防止医疗数据被篡改、泄露的医疗系统,可用来解决这些医疗难题.与现有医疗区块链系统相比,本系统具有一定的优越性与较好的适用性.Abstract: Medical data sharing, anti-tampering, and anti-leakage have always been difficult problems in medical industry. When a patient is on referral, he or she often can not provide information on previous visits. The reason is that many hospitals in China can not share medical information in most cases, and they can only pass the easily lost paper information such as medical records and checklists to achieve part of the medical information sharing. On the other hand, the patient's medical information is easy to leak, and medical information provided in a medical dispute can not be guaranteed in terms of authenticity and impartiality. In this research, an alliance medical blockchain system based on the practical Byzantine fault tolerance algorithm (PBFT) is designed, which is a multi-node maintenance and sharing system, and is able to prevent medical data from being tampered with or leaked. This medical system can be used to solve the above medical problems. Compared with the existing medical blockchain systems, this system has some advantages and good applicability.
-
Key words:
- Medical blockchain /
- medical data /
- consensus algorithm /
- medical information sharing
1) 本文责任编委 袁勇 -
表 1 Medical chain与现有医疗区块链对比
Table 1 Medical chain vs. existing medical blockchain
系统 基于区块链 共识机制 算法类型 支付报酬 需要节点数 算力需求 投票权比重设定 MDSM 是 改进DPOS POX 否 121个 小 是 MedRec 是 POW POX 是 多 大 否 ModelChain 是 POI POX 是 多 大 否 Medical chain 是 改进PBFT BFT 否 少, 至少4个 小 否 表 2 医疗信息化问题与Medical chain应对方式
Table 2 Medical informatization issues and medical chain's solutions
类型 面临问题 应对方式 隐私与安全 恶意攻击医疗数据保护不可抵赖性 将访问控制信息和每次的操作都加入到区块链中, 并且采用非对称加密机制, 能够保证患者的隐私不会受到威胁, 并且无法抵赖 患者参与度 患者难以获取自己的数据每到一家医院需要重新办理就诊卡, 流程繁琐 患者可以在一个平台上查看自己在各家医院的就诊记录, 并且可以隐藏自己相关的医疗信息来保护自己的隐私 数据访问性 医疗研究人员获取医疗数据困难患者获取自己在各医院的就诊记录困难医生获取患者之前的医疗信息困难 采用匿名形式以及访问控制来保证相关研究人员在得到授权后, 可以访问部分医疗信息, 患者可以查看到自己所有的医疗记录, 医生在患者授权下可以访问患者之前的医疗信息 医疗纠纷 在医院与患者发生医疗纠纷时, 医院与患者提供的证据难以确保其真实性 通过数字签名将相关医疗信息及其修改记录存储在区块链中, 确保证据的不可抵赖与真实性 -
[1] 蔡维德, 郁莲, 王荣, 刘娜, 邓恩艳.基于区块链的应用系统开发方法研究.软件学报, 2017, 28(6):1474-1487 http://d.old.wanfangdata.com.cn/Periodical/rjxb201706010Tsai Wei-Tek, Yu Lian, Wang Rong, Liu Na, Deng En-Yan. Blockchain application development techniques. Journal of Software, 2017, 28(6):1474-1487 http://d.old.wanfangdata.com.cn/Periodical/rjxb201706010 [2] Nakamoto S. Bitcoin: a peer-to-peer electronic cash system[Online], available: https://bitcoin.org/bitcoin.pdf, August 19, 2018 [3] 袁勇, 王飞跃.区块链技术发展现状与展望.自动化学报, 2016, 42(4):481-494 http://www.aas.net.cn/CN/Y2016/V42/I4/481Yuan Yong, Wang Fei-Yue. Blockchain:the state of the art and future trends. Acta Automatica Sinica, 2016, 42(4):481 -494 http://www.aas.net.cn/CN/Y2016/V42/I4/481 [4] Lamport L, Shostak R, Pease M. The Byzantine generals problem. ACM Transactions on Programming Languages and Systems (TOPLAS), 1982, 4(3):382-401 doi: 10.1145/357172.357176 [5] 韩璇, 刘亚敏.区块链技术中的共识机制研究.信息网络安全, 2017, (9):147-152 doi: 10.3969/j.issn.1671-1122.2017.09.034Han Xuan, Liu Ya-Min. Research on the consensus mechanisms of blockchain technology. Netinfo Security, 2017, (9):147-152 doi: 10.3969/j.issn.1671-1122.2017.09.034 [6] Bitshares.org. Delegated proof-of-stake consensus[Online], available: https://bitshares.org/technology/delegated-proof-of-stake-consensus/, July 10, 2018 [7] Castro M, Liskov B. Practical Byzantine fault tolerance and proactive recovery. ACM Transactions on Computer Systems (TOCS), 2002, 20(4):398-461 doi: 10.1145/571637.571640 [8] 薛腾飞, 傅群超, 王枞, 王新宴.基于区块链的医疗数据共享模型研究.自动化学报, 2017, 43(9):1555-1562 http://www.aas.net.cn/CN/abstract/abstract19131.shtmlXue Teng-Fei, Fu Qun-Chao, Wang Cong, Wang Xin-Yan. A medical data sharing model via blockchain. Acta Automatica Sinica, 2017, 43(9):1555-1562 http://www.aas.net.cn/CN/abstract/abstract19131.shtml [9] Wood G. Ethereum: a secure decentralised generalised transaction ledger[Online], available: http://gavwood.com/paper.pdf, August 19, 2018 [10] Azaria A, Ekblaw A, Vieira T, Lippman A. MedRec: using blockchain for medical data access and permission management. In: Proceedings of the 2nd International Conference on Open and Big Data (OBD). Vienna, Austria: IEEE, 2016.25-30 [11] Ivan D. Moving toward a blockchain-based method for the secure storage of patient records[Online], available: https://www.healthit.gov/sites/default/files/9-16-drew_ivan_20160804_blockchain_for_healthcare_final.pdf, August 19, 2018 [12] Shrier A A, Chang A, Diakun-thibault N, et al. Blockchain and health IT: algorithms, privacy, and data[Online], available: http://www.truevaluemetrics.org/DBpdfs/Technology/Blockchain/1-78-blockchainandhealthitalgorithmsprivacydata_whitepaper.pdf, August 19, 2018 [13] Kuo T T, Hsu C N, Ohno-Machado L. ModelChain: decentralized privacy-preserving healthcare predictive modeling framework on private blockchain networks[Online], available: https://www.healthit.gov/sites/default/files/10-30-ucsd-dbmi-onc-blockchain-challenge.pdf, August 19, 2018 [14] Witchey N. Healthcare Transaction Validation Via Block-chain Proof-of-Work, Systems and Methods, WIPO Patent Application WO/2015/175722, November 2015. [15] Rivest R. The MD5 message-digest algorithm. RFC, 1992, 473(10):492 http://d.old.wanfangdata.com.cn/OAPaper/oai_doaj-articles_f659b1885fb8206e9d53960c7f2f1fec [16] Eastlake D 3rd, Hansen T. US secure hash algorithms (SHA and HMAC-SHA)[Online], available: https://www.rfc-ed-itor.org/rfc/pdfrfc/rfc4634.txt.pdf, August 19, 2018 [17] Merkle R C. A digital signature based on a conventional encryption function. In: Proceedings of the 1987 Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg, Berlin, Germany: Springer, 1987.369-378 [18] Rivest R L, Shamir A, Adleman L M. Cryptographic Communications System and Method, USA Patent 4405829, September 1983. [19] Kravitz D W. Digital Signature Algorithm, USA Patent 5231668, July 1993. [20] Johnson D, Menezes A, Vanstone S. The elliptic curve digital signature algorithm (ECDSA). International Journal of Information Security, 2001, 1(1):36-63 http://d.old.wanfangdata.com.cn/OAPaper/oai_pubmedcentral.nih.gov_3821297 [21] 张明德, 刘伟. PKI/CA与数字证书技术大全.北京:电子工业出版社, 2015.22-25Zhang Ming-De, Liu Wei. PKI/CA and Digital Certificate Technology. Beijing:Publishing House of Electronics Industry, 2015.22-25 [22] Josefsson S. The base16, base32, and base64 data encodings[Online], available: https://www.rfc-editor.org/rfc/pdfrfc/rfc4648.txt.pdf, August 19, 2018 [23] 董建成.我国医院信息系统现状及原因分析.中华医院管理杂志, 2003, 19(4):228-230 doi: 10.3760/j.issn:1000-6672.2003.04.014Dong Jian-Cheng. Analysis of status and causes of hospital information system in China. Chinese Journal of Hospital Administration, 2003, 19(4):228-230 doi: 10.3760/j.issn:1000-6672.2003.04.014 [24] National Health Commission of the People's Republic of China. Electronic medical record basic architecture and data standards (Trial)[Online], available: http://www.moh.gov.cn/mohbgt/s6718/200912/45414.shtml, August 19, 2018 [25] Goda K. Storage area network. Encyclopedia of Database Systems. Boston, MA, USA:Springer, 2009.335-336 [26] Castro M, Liskov B. A Correctness Proof for a Practical Byzantine-Fault-Tolerant Replication Algorithm. Massachusetts Institute of Technology, Cambridge, MA, USA, 1999. [27] 结城浩[著], 周自恒[译].图解密码技术.第2版.北京: 人民邮电出版社, 2016.Yuki H[Author], Zhou Zi-Heng[Translator]. Graphical Cryptography. Beijing: The People's Posts and Telecommunications Press, 2016. [28] Galperin S, Malpani A, Adams C, Ankney R, Santesson S, Myers M. X.509 Internet Public Key Infrastructure Online Certificate Status Protocol-OCSP, RFC 6960, 1999. [29] 李凤华, 苏铓, 史国振, 马建峰.访问控制模型研究进展及发展趋势.电子学报, 2012, 40(4):805-813 doi: 10.3969/j.issn.0372-2112.2012.04.030Li Feng-Hua, Su Mang, Shi Guo-Zhen, Ma Jian-Feng. Research status and development trends of access control model. Acta Electronica Sinica, 2012, 40(4):805-813 doi: 10.3969/j.issn.0372-2112.2012.04.030 [30] Szabo N. Formalizing and securing relationships on public networks. First Monday, 1997, 2(9):1-21 [31] Etherscan.io. Ethereum network HashRate growth chart[Online], available: https://etherscan.io/chart/hashrate, August 19, 2018 [32] Bitcoin cash charts[Online], available: https://charts.bitcoin.com/chart/hash-rate, August 19, 2018 [33] Etherscan.io. Ethereum block difficulty growth chart[Online], available: https://etherscan.io/chart/difficulty, August 19, 2018 [34] Wang S, Jiang X Q, Wu Y, Cui L J, Cheng S, Ohno-Machado L. EXpectation propagation LOgistic REgRession (EXPLORER):distributed privacy-preserving online model learning. Journal of Biomedical Informatics, 2013, 46(3):480-496 http://d.old.wanfangdata.com.cn/NSTLQK/NSTL_QKJJ0231223213/ [35] Yan F, Sundaram S, Vishwanathan S V N, Qi Y. Distributed autonomous online learning:regrets and intrinsic privacy-preserving properties. IEEE Transactions on Knowledge and Data Engineering, 2013, 25(11):2483-2493 doi: 10.1109/TKDE.2012.191 -




 下载:
下载: